Link manipulation: What is it and how to stay safe

Link manipulation is a common tactic used by cybercriminals: they trick people into visiting harmful sites by disguising phishing links to look like trusted sites. These manipulated links can expose you to serious security and privacy threats, often without you ever realizing it.
Whether you're a casual web user, a marketer, or a site owner, this guide will offer some practical tips, real-world examples, and expert advice to help you recognize and avoid link-based threats before they cause harm.
What is link manipulation?
Link manipulation uses fake or deceptive URLs to trick people into visiting harmful websites. These links often show up in emails, texts, or social media messages and are crafted to look nearly identical to legitimate ones. When clicked, they can redirect you to sites that steal personal information, install malware, or carry out other malicious activities.
The practice gained traction back in the early to mid-2000s, as cybercriminals saw an opportunity to exploit the growing reliance on email for everyday communication.
By hiding malicious URLs behind seemingly harmless links, attackers trick people into clicking and exposing themselves to threats. This quickly became a common method for delivering scams and malware.
Why link manipulation is a growing threat
Link manipulation is a growing threat because attackers are finding more sophisticated ways to exploit trust, deceive users, and bypass traditional security tools.
One emerging concern is the abuse of URL rewriting, a feature used by email security vendors to scan links for threats. Attackers have found ways to weaponize it, delivering phishing links that bypass even advanced security systems.
At the same time, older techniques haven’t gone away; they’ve simply become more sophisticated. Attackers now target everyone from casual surfers to network infrastructure professionals, constantly refining their methods to stay ahead of defenses.
Where link manipulation occurs
Link manipulation commonly appears across multiple platforms where you’re likely to click on links without inspecting them closely.
| Source | How link manipulation happens |
| Emails | Many phishing attacks happen via email. The attacker sends links that may look like they come from trusted senders but lead to fake websites. Learn more by checking out our page dedicated to URL phishing attacks. |
| Websites | Malicious links may appear on compromised websites, in fake pop-ups, or embedded in malicious ads (malvertising). These can redirect you to scam or malware-laden pages. |
| Social media | Attackers use fake accounts or hijacked profiles to post shortened or spoofed links, often disguising harmful destinations behind clickbait or trending topics. |
| Search engines (SEO abuse) | Cybercriminals use black-hat search engine optimization (SEO) techniques (unethical tactics like keyword stuffing) to manipulate search results so that malicious websites rank higher and appear legitimate when you search for popular topics. |
The goal is the same in all these spaces: to get you to click without questioning where the link actually leads.
Common link manipulation techniques
Typosquatting and misspelled URLs
Typosquatting is an illegal type of link manipulation that relies on users making small typing errors, often just one misplaced letter, to phish or scam them. This technique gained traction in the early 2000s when domain names became cheap and easy to register.
Scammers register domain names that feature slight misspellings or variations of legitimate websites. They then create fake sites that closely mimic the originals. Their goal is to deceive people into entering passwords, credit card numbers, or other sensitive information.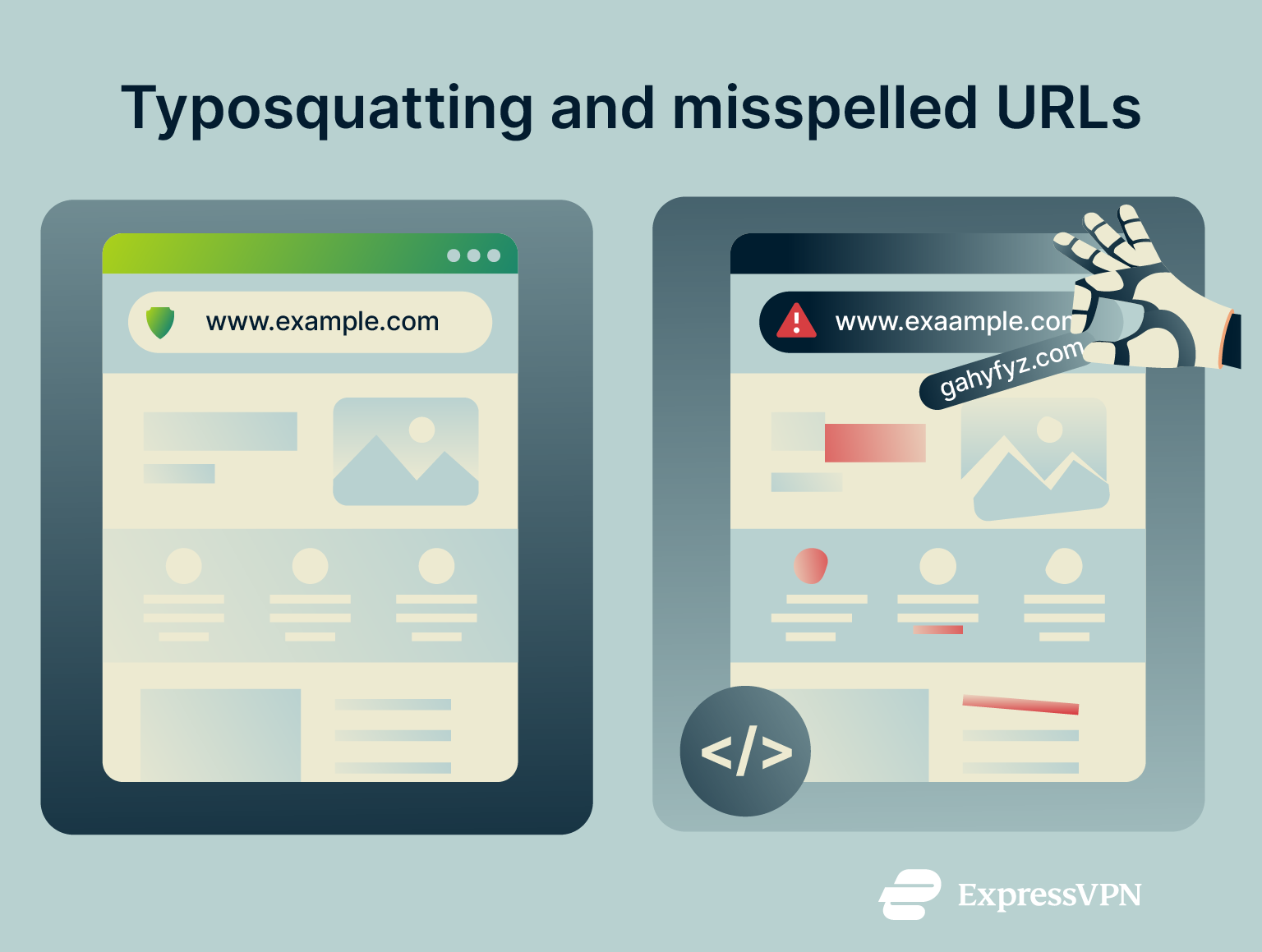 Generative AI has exacerbated this problem. Scammers now use algorithms to quickly generate lists of convincing imitation domains. Techniques include adding or removing dashes (_ or -), swapping characters, using incorrect or additional top-level domains (TLDs), and replacing vowels.
Generative AI has exacerbated this problem. Scammers now use algorithms to quickly generate lists of convincing imitation domains. Techniques include adding or removing dashes (_ or -), swapping characters, using incorrect or additional top-level domains (TLDs), and replacing vowels.
To fight back, many companies register multiple variants of their domain names to block scammers. However, with countless ways to misspell a name, typosquatting remains difficult to police.
Punycode (IDN) spoofing
A more advanced version of typosquatting is Internationalized Domain Name (IDN) spoofing. This scam is sometimes referred to as a homograph or homoglyph attack and uses lookalike characters (known as Unicode Confusables) from other alphabets to create fake domains that appear legitimate.
Attackers use special characters from other languages that resemble English letters. Here’s how it’s possible:
- The internet supports IDNs, which let websites use characters from non-English languages (like Cyrillic, Greek, or Chinese).
- Some of these characters look very similar to English letters. For example, the Cyrillic “а” looks just like the Latin “a,” the Cyrillic “e” looks just like the Latin “e,” and the small Roman ten “x” looks just like “x.”
- An attacker registers a domain using these lookalike letters. The address will look the same, but it’s a completely different site.
Some attackers don’t even need foreign characters; they rely instead on visually similar English letters (for example, swapping a lowercase “l” with a capital “I” to turn “login.com” into “Iogin.com”).
Once IDNs became easy to register, attackers started exploiting them. While browsers have added defenses against Punycode attacks, they still occur frequently due to differences in how browsers handle IDNs. After all, special characters can sometimes serve legitimate purposes. For example, languages like German use characters such as 'ä', 'ö', and 'ü', which are used in government websites.
Reflected link manipulation
Reflected link manipulation makes a malicious link appear to come from a trusted site. Attackers target sites that don’t properly filter or sanitize user input and create special URLs that include malicious code or fake content, which the site then unknowingly displays to the user.
The attacker sends the link with false or misleading information, often via email. When clicked, the legitimate website displays part of the link, making it seem normal. Since the link includes a trusted website name, you may unknowingly enter sensitive information.
DOM-based link manipulation
Document Object Model (DOM)-based link manipulation tricks your browser into showing or doing something it shouldn’t by altering content on the client side, not the server.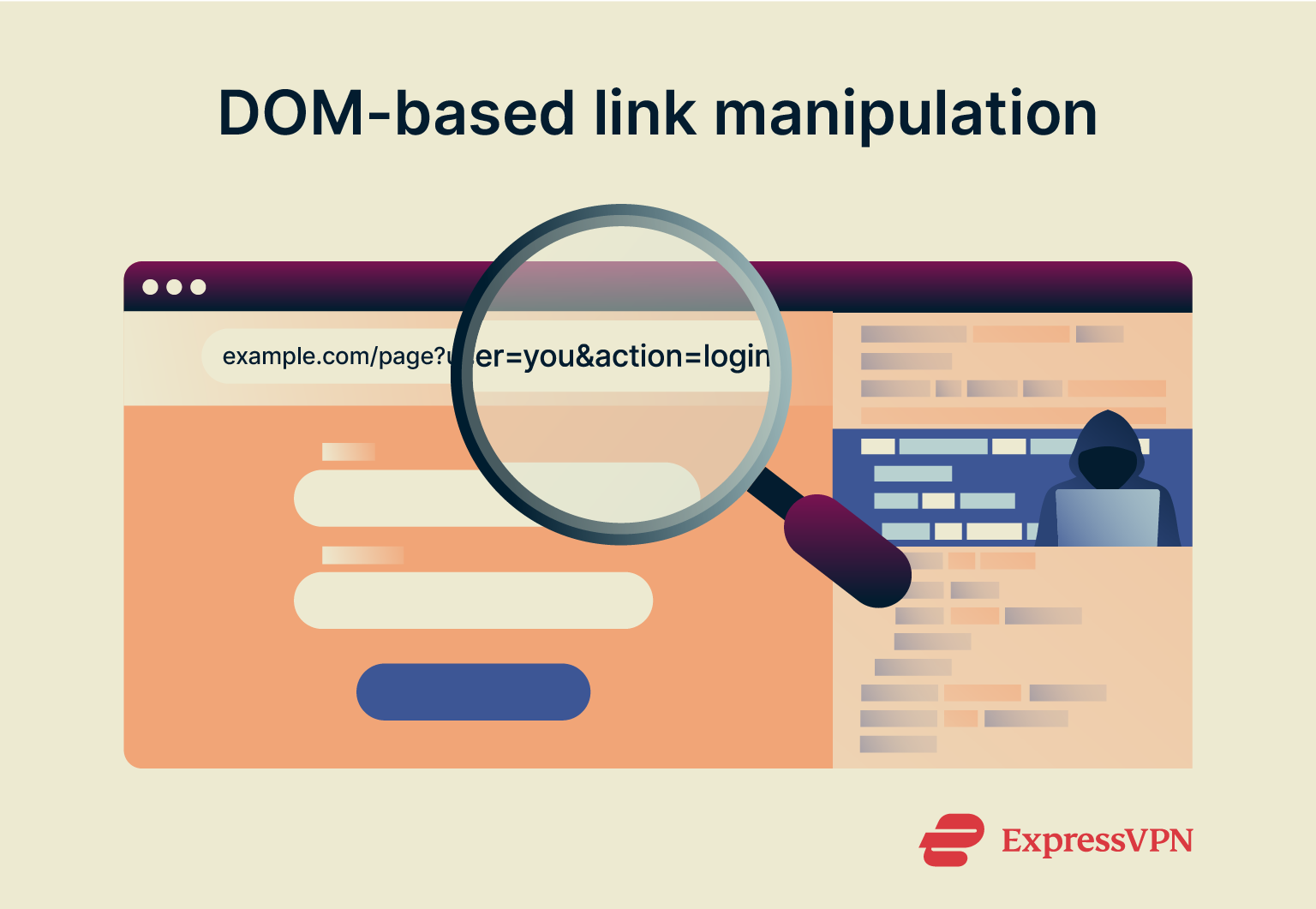 The attacker sends a seemingly normal link with hidden instructions in the URL. When clicked, your browser loads the real website but updates the page using parts of the URL. The attacker exploits this by injecting harmful content, such as a fake login form or a data-stealing link.
The attacker sends a seemingly normal link with hidden instructions in the URL. When clicked, your browser loads the real website but updates the page using parts of the URL. The attacker exploits this by injecting harmful content, such as a fake login form or a data-stealing link.
Phishing and social engineering via links
Phishing and social engineering are deceptive tactics used by cybercriminals to trick people into revealing sensitive information. This includes login credentials, personal data, financial details, and other information that may help the scammer get your money.
These attacks often start with a fake email that looks like it’s from someone you trust: a bank, a friend, or a well-known company. The email will use urgency (e.g., “Your account is locked! Click here to fix it”) to prompt you to act impulsively. Social engineering involves various manipulation tactics, so it's important to learn about other common methods these attackers use to trick you.
Once you land on the fake page, you might be asked to enter personal info like login details or credit card numbers. If you do, hackers can steal your identity, access your accounts, or even sell your data to other criminals.
Hidden links and cloaked URLs
Hidden links and cloaked URLs deceive users and redirect them to malicious websites or content without their knowledge. Here’s how:
- Hidden links: These are links that are purposely disguised or hidden from view on a webpage. For instance, they might be the same color as the background, making them invisible to the user, or they could be placed in areas that are hard to spot.
- Cloaked URLs: This technique involves showing a different URL to users than the actual destination. For example, a link might appear to go to a trusted website, but the actual link is masked to redirect you to a malicious site.
Open redirect exploits
An open redirect exploit happens when an attacker sends a link to a trusted website with a redirection to a malicious site, like “https://example.com?redirect=http://www.maliciouswebsite.com/”. When clicked, you land on the trusted site, making the link seem legitimate. But soon after, you're redirected to the malicious site.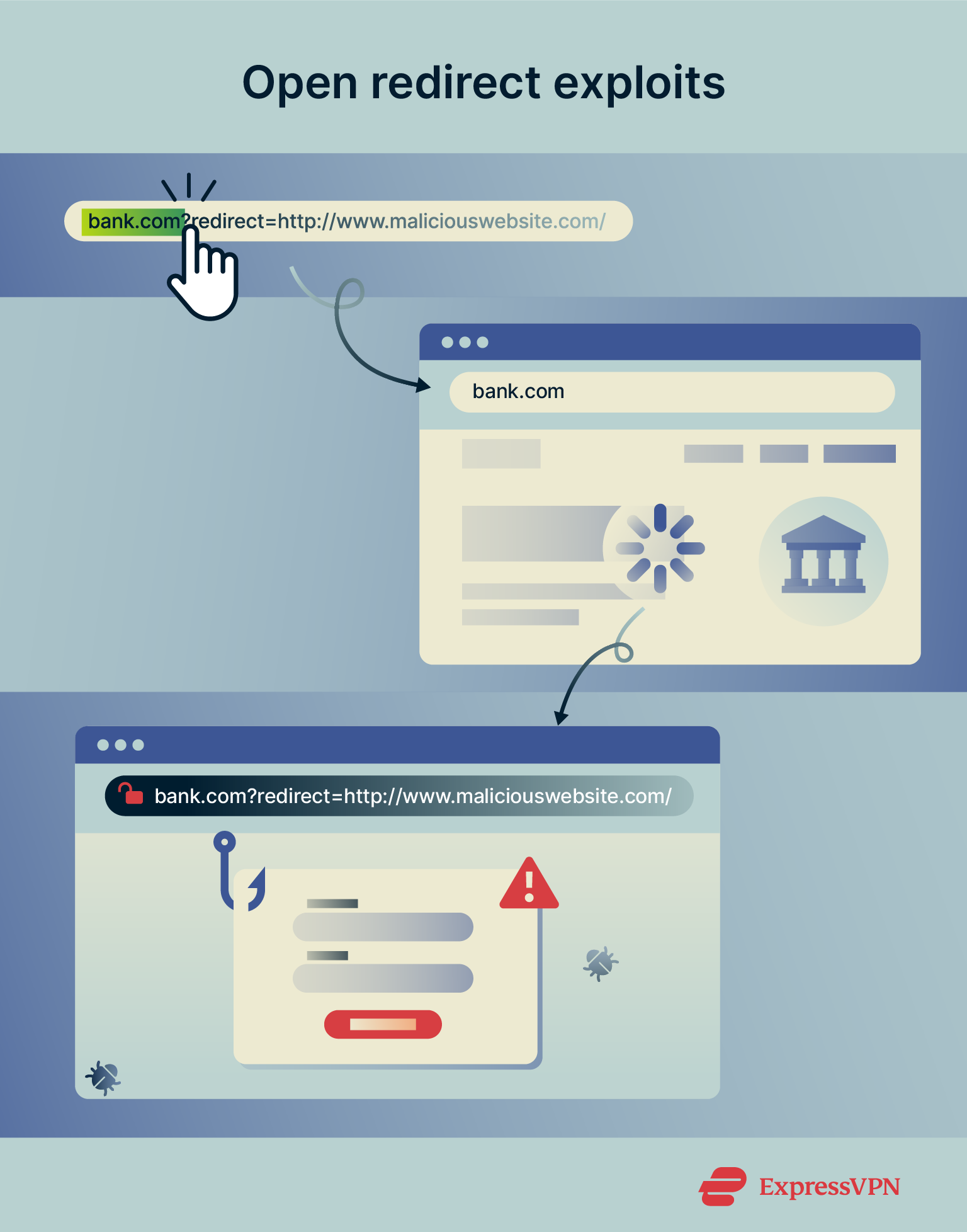 Attackers commonly use open redirect exploits in phishing attacks to trick users into visiting malicious sites.
Attackers commonly use open redirect exploits in phishing attacks to trick users into visiting malicious sites.
URL obfuscation and redirection tactics
URL obfuscation involves altering or encoding a URL to make it look legitimate while hiding its true destination. Attackers use this tactic to disguise malicious links and bypass security filters.
For example, they might replace characters with similar-looking ones or use URL encoding to confuse both users and security systems. A URL like “https://example.com/secure” might be obfuscated to look like “https://example.com/%73ecure,” making it hard for the user to notice the difference.
Link farming and paid backlink schemes (SEO abuse)
Link farming and paid backlink schemes are tactics used to manipulate search engine rankings by creating an artificial network of links. In link farming, multiple low-quality sites link to each other to boost their SEO rankings, while paid backlinks involve purchasing links from other websites to artificially increase visibility.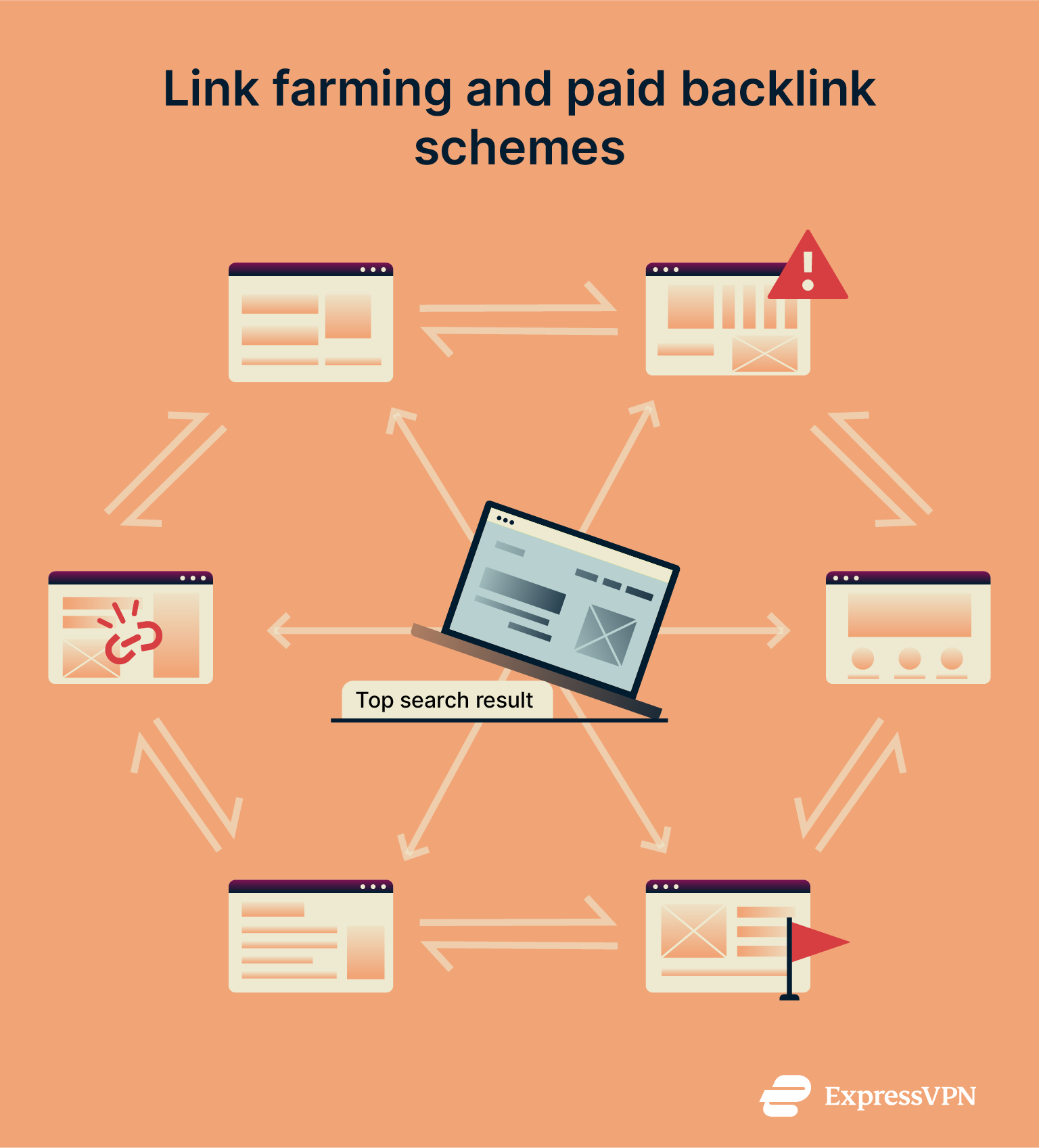 These practices deceive search engines into thinking a site is more reputable than it is, often leading to spam or malicious sites appearing higher in search results.
These practices deceive search engines into thinking a site is more reputable than it is, often leading to spam or malicious sites appearing higher in search results.
Real-life examples of link manipulation
From high-profile phishing scams to social engineering campaigns, link manipulation affects individuals and businesses alike. Below are some of the most notable examples of link manipulation.
High-profile phishing campaigns
Various companies have been the targets of phishing campaigns, the most recent one being Twitter (now X) in 2020. The campaign targeted high-profile accounts like Elon Musk, Barack Obama, and Joe Biden using Twitter's internal tools.
After a series of phishing attacks targeted at Twitter employees, attackers gained access to Twitter's internal tools. They then hijacked prominent Twitter accounts to post a scam, promising to double any Bitcoin sent to a specific wallet address. The attackers stole over $100,000 in Bitcoin before X (then Twitter) regained control.
Similarly, during the early stages of the COVID-19 pandemic, a group of scammers spread phishing emails with urgent and fear-based messaging about the virus to trick people into clicking malicious links.
Some emails claimed to be from the World Health Organization (WHO) or the Centers for Disease Control and Prevention (CDC), offering safety guidelines or fake virus tracking tools that led to credential theft or malware installation.
SEO spam incidents
One of the most infamous examples of this is a campaign that used paid ads to promote a fake Google Authenticator website. Cybercriminals exploited Google Ads to push their malicious site to the top of search results, making it appear more legitimate than the official page.
The site was nearly identical to the real Google Authenticator landing page, making it extremely difficult for users to spot any red flags. Victims who clicked the ad were prompted to download what they thought was the official two-factor authentication app. Instead, they received malware.
Once installed, the malware could steal sensitive information, monitor user activity, or even grant attackers full control of the infected device, illustrating just how dangerous link manipulation can be when combined with tactics like ad spoofing and domain impersonation.
Risks of link manipulation
Data theft and malware
By tricking you into clicking manipulated links, attackers can infect your device with malware. They can also gain access to sensitive personal or financial data, such as login credentials or credit card details, by tricking you with a legitimate-looking site. Once they have this information, they can steal identities, make fraudulent transactions, or use the data for further attacks.
Brand reputation damage
For businesses, link manipulation can severely damage brand reputation. If users are tricked into visiting a fake website or falling for a phishing scam, they may lose trust in the company that was being imitated. This can lead to a decline in customer loyalty, negative reviews, and long-term harm to the company’s public image.
Legal and compliance consequences
Businesses must also consider the legal and compliance risks that come with link manipulation. For example, if a company is found to be negligent in protecting its users from data theft, it could face legal action, regulatory fines, or being found in violation of data protection laws, such as the General Data Protection Regulation (GDPR). Failing to secure your data adequately could also lead to costly lawsuits and damage to the company’s reputation in the eyes of regulators.
How to identify and prevent link manipulation
There are several ways to identify and prevent link manipulation. By paying attention to specific signs, you can reduce the chances of falling victim.
Red flags in URLs
To avoid falling for link manipulation, it's important to closely examine URLs before clicking. Here are some common red flags:
- Spelling errors: If a URL contains odd misspellings, extra characters, or unusual domain names that look similar to trusted ones, it's a likely sign of manipulation.
- Shortened links: While shortened links like those from bit.ly or TinyURL can be convenient, they can also mask a dangerous destination. If you can, preview the link before clicking. Learn more about shortened link risks and how to stay safe.
- Suspicious TLDs: Pay attention to unusual TLDs like “.xyz” or “.ml,” which are often used by attackers to create lookalike domains. Trusted organizations tend to use standard TLDs such as “.com” or “.org.”
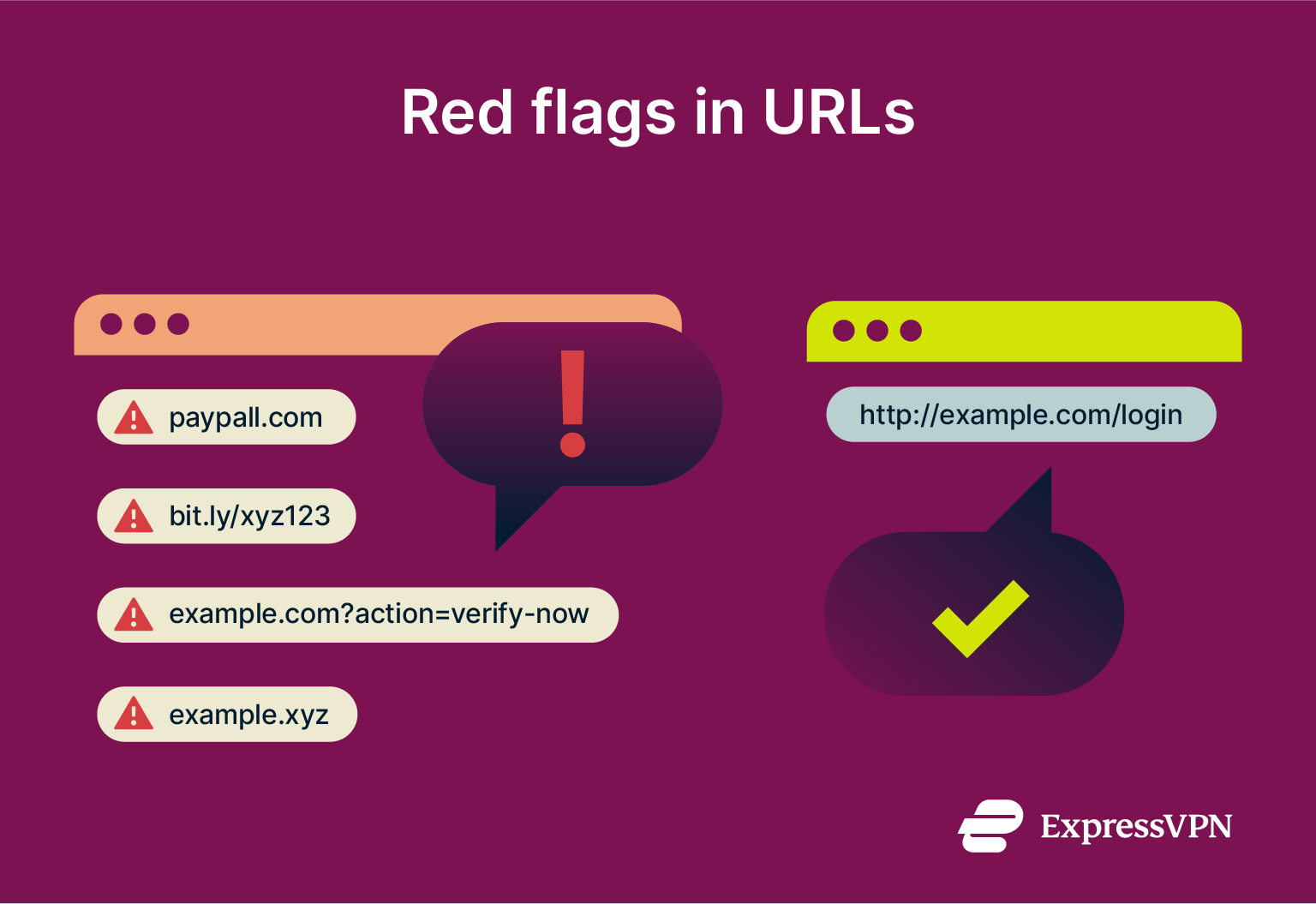
How to check if a link is safe
If you’re unsure whether a link is legit, here are some basic steps you can take to check:
- Hovering over links: Hover your mouse over a link to preview the full URL. This can reveal discrepancies between what’s displayed and where the link actually leads.
- Check the HTTPS connection: Ensure the website uses HTTPS (look for the padlock icon next to the URL). While not foolproof, HTTPS helps ensure that data between your browser and the site is encrypted.
- Cross-check the URL: Compare the link to the official website by typing the official website URL manually into your browser. Scammers often create URLs that look similar to trusted sites but with subtle differences (like letter changes or added subdomains).
Tools and extensions for detection
Use link checkers, security extensions, or URL scanners to verify a URL’s safety. These tools flag phishing sites and malware. Also, use an up-to-date browser from a trusted developer: most will warn you about dangerous websites.
Additionally, you can use ExpressVPN’s Advanced Protection feature to prevent you from accidentally accessing malicious sites. It’s convenient because it automatically blocks malicious sites, harmful links, and ads to help you stay safe online. Just turn it on in the settings and connect to a server.
Manual vs. automated methods
There are two main ways to protect yourself from link manipulation: manual checks and automated tools. For the strongest defense, it's best to use a combination of both.
| Manual methods | Automated methods |
| Look over the URL carefully to check for red flags | Use browser extensions, anti-phishing software, or online tools that automatically scan links for potential threats |
| Check the website’s design and grammar for signs of phishing | Enable built-in browser protection features (like Google Safe Browsing or SmartScreen) |
| Verify the URL’s legitimacy by contacting the organization directly through official channels | Use website reputation services or monitoring tools that alert you to spoofed domains |
Educating teams and end users
 Phishing is responsible for a substantial portion of cyberattacks, with estimates suggesting that 80-95% of all cyberattacks begin with phishing attempts. As such, it’s important to educate your team and family members about link manipulation.
Phishing is responsible for a substantial portion of cyberattacks, with estimates suggesting that 80-95% of all cyberattacks begin with phishing attempts. As such, it’s important to educate your team and family members about link manipulation.
- Train employees: Regularly train staff on the dangers of link manipulation and how to spot suspicious hyperlinks. Awareness of phishing tactics, URL manipulation, and social engineering is key to preventing these attacks.
- Promote safe browsing habits: Encourage users to follow best practices like verifying URLs, avoiding suspicious emails, and using strong, unique passwords. In addition, educate them about browser security features such as "safe browsing" modes and security alerts.
- Simulate phishing attacks: For organizations, running simulated phishing campaigns can help employees recognize phishing attempts and avoid falling for manipulative tactics.
By using these preventive measures, you can greatly reduce the risk of link manipulation attacks. It's also important to learn how to identify safe websites: look for secure connections and trusted domains to protect yourself from scams, malware, and other online threats.
Is link manipulation illegal?
Link manipulation can be illegal depending on its use and intent. While not all instances are unlawful, like URL shortening and hyperlinks, many become illegal when used for phishing, data theft, or fraud. Below is an overview of legal definitions, gray areas, and regulations related to link manipulation.
Legal definitions and grey areas
Link manipulation often ties into broader crimes like fraud, identity theft, and unauthorized access. For example, using fake URLs to trick users into clicking with the intent to steal data or install malware is typically considered fraud.
One grey area is when a link is intentionally altered to drive traffic to certain websites for financial gain. While this can be unethical and violate terms of service agreements, it may not always be classified as illegal unless it’s part of a larger fraudulent scheme.
Relevant regulations
Various regulations and laws touch on activities related to link manipulation:
- General Data Protection Regulation (GDPR): Under GDPR, the unauthorized collection or processing of personal data is illegal. If link manipulation is used to deceive users into providing personal information (such as through phishing), it could be considered a violation of the GDPR, particularly if personal data is misused or exposed. It’s an EU regulation, but it applies to any entity that collects information from EU residents.
- Controlling the Assault of Non-Solicited Pornography and Marketing (CAN-SPAM) Act: In the U.S., this law regulates commercial email, banning misleading subject lines, sender info, and deceptive practices. If a manipulated link is used to trick recipients into clicking malicious links, the sender could violate this law.
- Computer Fraud and Abuse Act (CFAA): The CFAA criminalizes unauthorized access to computer systems in the U.S. If link manipulation is used to trick users into accessing a malicious website, or if a hacker uses it to gain unauthorized access to systems or data, they could be prosecuted under the CFAA.
When it becomes a cybercrime
Link manipulation becomes a cybercrime when it is used maliciously to deceive users, exploit vulnerabilities, or commit fraud.
| Category | Description | Risks/Consequences |
| Phishing attacks | Use of link manipulation (e.g., typosquatting, subdomain spoofing, URL obfuscation) in phishing campaigns to trick users into clicking malicious links. | Theft of login credentials, credit card info, or personal data; identity theft; fraud. |
| Exploitation of vulnerabilities | Involves injecting malicious code into URLs (DOM-based or reflected) or manipulating HTTP headers/form actions to exploit web app vulnerabilities. | Redirects to phishing sites; data leaks; bypassing security; violation of cybersecurity laws. |
| Unauthorized access | Altering URL parameters to bypass authentication and gain access to secure systems. | Considered hacking; violates laws like the CFAA in the U.S. |
| Fraudulent redirection | Use of manipulated links to redirect users for fraudulent purposes, such as intercepting transactions or diverting payments. | Financial loss for individuals and organizations; a common tactic in cybercrime. |
Combat link manipulation with the right tools
Using the right tools can be crucial to protect against link manipulation. Here are a few that can help.
Browser extensions
Browser extensions are one of the easiest ways to enhance your security and detect suspicious links. Here are some helpful ones to get you started:
- Link Unshortener: Expands shortened URLs to reveal their true destination, helping you avoid deceptive or malicious links.
- NoScript Security Suite: Allows you to control which scripts run on websites, preventing clickjacking and other script-based attacks.
- Privacy Badger: Automatically blocks invisible trackers and spying ads, enhancing your privacy and security online.
These tools can alert you when a link is suspicious or leads to a known malicious site and block pop-ups, making it harder for attackers to manipulate links undetected.
Anti-phishing software
Anti-phishing software scans emails and websites for known phishing patterns. These tools can detect and block links that have been manipulated to look like legitimate ones but lead to fake or harmful websites. Anti-phishing software often includes real-time alerts to notify you of potential threats, helping you avoid falling for phishing scams that rely on link manipulation. Many email clients and web browsers integrate anti-phishing capabilities, but anti-phishing software like ExpressVPN’s Advanced Protection offers additional layers of protection against malicious sites.
Anti-phishing software often includes real-time alerts to notify you of potential threats, helping you avoid falling for phishing scams that rely on link manipulation. Many email clients and web browsers integrate anti-phishing capabilities, but anti-phishing software like ExpressVPN’s Advanced Protection offers additional layers of protection against malicious sites.
SEO auditing tools
For webmasters and businesses, SEO auditing tools can help spot link manipulation techniques, such as cloaking, keyword stuffing, or unnatural link patterns. These tools scan your site for suspicious backlinks and provide insights into how manipulative tactics could be affecting your website's search rankings.
Regular SEO audits can ensure that your website isn’t negatively impacted by malicious actors who attempt to manipulate search engine results using deceptive URLs or exploit your domain’s reputation.
Domain monitoring services
Domain monitoring services help track any unauthorized changes or manipulations of your domains. These tools alert you to any suspicious registrations of look-alike domains or subdomains that could be used for phishing attacks.
Actively monitoring your domain and related URLs helps you spot counterfeit sites early and protect against brand impersonation that could damage your reputation or mislead users.
Note: The web is full of malicious actors and cyber threats; as such, prevention is key. To protect yourself, check out our guide to online safety.
FAQ: Common questions about link manipulation
How can I tell if a link is fake?
Always hover over the link before clicking to see the actual URL. If it’s shortened or if you’re pressured to click quickly, it might be a phishing attempt. Additionally, if the link takes you to an unfamiliar site, that’s a red flag.
How do hackers hide malicious links?
What should I do if I click a malicious link?
If the link was to a phishing site, change your passwords, especially for compromised accounts. Contact your bank or other relevant entities if you entered any sensitive information. Lastly, report the attack to the proper authorities or your IT team if you're in a business setting.
Can link manipulation hurt my SEO?
Is link manipulation legal?
What tools can detect link manipulation?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN