Security concerns in cloud computing and how to address them

Cloud computing has transformed how organizations store data, build software, and manage everyday operations. It offers unmatched flexibility and scalability compared to traditional on-premises systems.
But with these benefits come new security challenges. Cloud security is a shared responsibility: providers protect the infrastructure, while customers must secure their own data with the proper protections and configurations. A single mistake on either side, like misconfigured settings or an API vulnerability, can expose the entire system.
In this guide, we’ll explore the main security risks in cloud computing and show you how to protect your data effectively.
What are the main security concerns in cloud computing?
Cloud environments create new types of risks that often go unnoticed until something goes wrong. The most common security concerns fall into these categories:
- Data exposure: Sensitive information stored or shared in the cloud can be exposed through weak encryption, insecure data sharing, or accidental leaks.
- Access control: Poor identity management, weak passwords, or excessive permissions can allow unauthorized access to critical resources.
- Infrastructure management: Unpatched software, overlooked dependencies, and rapid scaling can introduce vulnerabilities.
Addressing these risks requires proactive security practices. According to IBM's Cost of a Data Breach Report, the average cost of a cloud-based data breach in 2025 is $4.4 million, showing that prevention is far more cost-effective than recovery.
Why cloud security matters today
Cloud security matters because many modern businesses run on cloud services. Websites, payment processing, data storage, and more all take place in the cloud. All this infrastructure needs to be carefully secured, as attacks can put the business and their clients or customers at risk.
In addition, due to the interconnected nature of cloud services, if cybercriminals compromise one cloud system, they may be able to access data from others as well. In some circumstances, a single vulnerability can cascade across multiple organizations.
Remote work, third-party integrations, and automation tools only increase the complexity of cloud security, making it harder to see where sensitive data lives and who has access to it.
Learn more: For broader context, read our guide to internet infrastructure, which goes into more depth about where cloud services fit in.
Cloud deployment models and their security implications
There are several types of clouds, each with its own advantages:
- Public cloud: Services that are delivered over shared networks that host multiple clients. Popular examples include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. Misconfigurations in public clouds are particularly dangerous because resources often sit directly on the public internet. If access controls or authentication are weak, data and services can easily be compromised by cybercriminals.
- Private cloud: An organization builds a private cloud on-site or through a dedicated provider. It can be fully customized and include specific compliance oversight, making it a good option for industries such as finance or healthcare. The downside is that they’re expensive and require dedicated cloud experts to ensure uptime and monitor threats.
- Hybrid cloud: A hybrid setup combines public and private environments to get the best of both worlds. For example, businesses can keep critical operations on a private cloud while using the public cloud for additional resources. Data moving between the two clouds requires encryption to prevent security gaps.
- Community cloud: A community cloud is shared by multiple organizations with similar goals or regulatory requirements, such as hospitals, universities, or government agencies. It allows members to collaborate securely and share computing resources under a common policy framework. However, if one member fails to follow proper security or compliance practices, the entire community environment can be exposed.
- Multi-cloud: A multi-cloud setup uses services from several cloud providers to distribute workloads and avoid dependency on a single provider. This approach increases flexibility and resilience but introduces complexity, as each provider has different security tools, policies, and configurations. Without unified visibility and consistent governance, security gaps can appear.
Most common cloud security threats
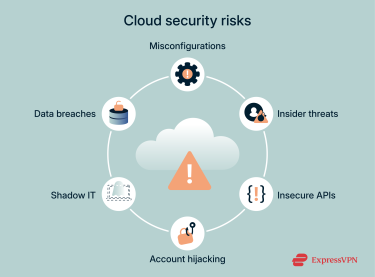
Data breaches
A data breach refers to an unauthorized user gaining access to sensitive information. This can occur due to weak passwords, unencrypted data, or unpatched vulnerabilities. Once a cybercriminal has access to sensitive data, they may leak it online, sell it on the dark web, or hold it at ransom.
Misconfigurations
Simple mistakes, such as leaving a storage bucket public or mismanaging access permissions, are among the top causes of cloud incidents. One overlooked setting can expose sensitive data to the public internet.
Insider threats
Employees, contractors, or administrators with legitimate access can intentionally or accidentally compromise systems. Without strong monitoring and access restrictions, a user can bypass safeguards that keep data secure. Insider threats are particularly dangerous because these users already have valid credentials and understand how systems work.
Insecure APIs
APIs are the backbone of cloud applications, enabling communication between systems. Weak authentication or poor input validation can expose sensitive data and provide access to the broader network.
As organizations adopt more microservices (applications split into many small services that talk to each other via APIs) and serverless architectures (small cloud-hosted functions triggered on demand), the number of APIs grows exponentially. Each one represents a potential entry point that needs proper authentication, rate limiting, and encryption.
Account hijacking
Cybercriminals use tactics like phishing, credential stuffing, or brute-force attacks to gain access to cloud accounts. Once inside, they can extract data, disrupt services, or impersonate legitimate users.
Shadow IT
Shadow IT refers to employees using unauthorized apps or cloud services without the company’s knowledge. Without oversight or proper controls, it creates compliance blind spots and increases the risk of data leaks.
Cloud vulnerabilities you should know
Understanding the weaknesses that can appear in a cloud setup helps you spot issues before they turn into serious problems. They can affect both public and private clouds, though they’re often most visible in shared or hybrid setups.
Many of these vulnerabilities aren’t unique to cloud computing. They’re common web or infrastructure flaws that become more critical in public cloud environments because of shared infrastructure, automation, and multi-tenancy.
Server-side request forgery (SSRF)
An SSRF attack happens when a hacker tricks a server into sending requests to internal systems it shouldn't access. In a cloud environment, this can expose metadata, credentials, or other sensitive resources.
The risk has grown with the rise of cloud-native apps, so much so that the Open Worldwide Application Security Project (OWASP) Top 10 lists SSRF as a critical web security issue. To prevent it, validate all external inputs and enforce strict network segmentation.
Incomplete data deletion
Deleting data in the cloud isn’t always as simple as pressing the delete button. Backups, snapshots, and cached copies can remain in storage systems long after removal.
To ensure data is truly gone, encrypt stored data and use your provider’s data deletion controls. Always verify that deleted data is removed from all backups and archived logs.
Multi-tenant architecture risks
In public and multi-cloud environments, multiple clients share the same physical infrastructure. If the isolation between tenants is compromised because of a platform bug or a misconfiguration, an attacker could potentially reach another client’s data.
To reduce this risk, providers and customers need strong logical separation controls, including encryption, strict identity and access management (IAM), and provider-level monitoring for suspicious cross-tenant activity.
Major cloud providers have these features available, but configuration errors on the customer side can expose data. Understanding how your provider implements tenant separation may help you assess and mitigate the above risks.
Open S3 buckets
Amazon S3 buckets and similar storage services are extremely convenient, but if they’re not properly configured, they can expose massive amounts of data. Attackers scan for these unsecured buckets, often discovering sensitive information within minutes. To limit the risk, run regular audits, enforce least-privilege access (only giving each user or application the minimum permissions it needs), and enable encryption by default. Automated scanning tools can also help identify exposed buckets before attackers do.
Serverless function vulnerabilities
Serverless computing platforms (such as AWS Lambda, Google Cloud Functions, and Azure Functions) let developers run code on demand without managing servers. These services are part of the cloud’s function-as-a-service (FaaS) model, where the provider handles infrastructure while customers secure their own code and permissions.
Security risks come from insecure coding practices, overprivileged roles, or outdated dependencies, any of which can give attackers access to connected cloud data or services. To reduce the risk, apply the principle of least privilege, scan code libraries for vulnerabilities, and monitor each function’s activity across your cloud environment.
Data protection and privacy in the cloud
Good passwords alone aren’t enough to keep sensitive data safe in the cloud. Robust protection comes from multiple layers working together: encryption, smart access controls, and reliable backup systems that you can count on when something goes wrong. Here’s how to build that defense.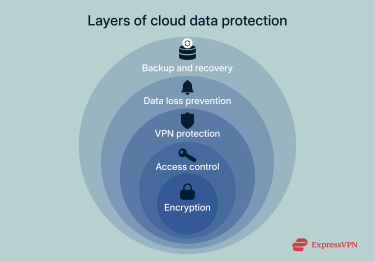
Backup and disaster recovery strategies
Rather than stealing data, sometimes attackers try to encrypt, corrupt, or destroy it. Ransomware, malicious insiders, and faulty updates can all make critical cloud data unavailable. A solid backup and disaster recovery plan is what lets you restore systems quickly after an attack and limit the damage.
A proven method is the 3-2-1 backup rule:
- Keep three copies of important data.
- Store them on two different types of media.
- Keep one copy off-site (or in a separate cloud region).
Regularly test your backups to ensure they can be restored when you actually need them.
Data loss prevention
The risk of data loss can be minimized by ensuring all data storage in the cloud is regularly audited to ensure proper configuration and access controls, secure API interactions, and that all third-party integrations are trusted and functioning normally.
Data loss prevention (DLP) tools can also help detect unusual activity (like someone downloading large volumes of data outside normal hours), but they’re only effective if configured and monitored correctly.
Role of VPNs in cloud access control
Virtual private networks (VPNs) help secure access to cloud resources by encrypting traffic between users, offices, and cloud environments. Cloud VPNs protect remote workers connecting to internal resources, ensuring private, authenticated communication between offices, data centers, and mobile users. Enterprise VPNs often form part of a zero-trust framework, which is used to verify every connection before granting them access to the cloud infrastructure.
Note: Commercial VPNs, like ExpressVPN, are different from the corporate VPNs described above. They are designed to protect personal privacy, secure online activity on public Wi-Fi, and to help users access the open internet more freely.
Identity and access management (IAM)
IAM defines who can access the cloud server and what they can do once they're inside. It answers three basic questions:
- Who are you?
- Should you be here?
- What are you allowed to access?
Strong IAM setups use multi-factor authentication (MFA), role-based permissions, and regular removal of old or inactive accounts. The principle is straightforward: give every user only the access they need to do their job. This ensures that if one account is compromised, the damage is limited and contained.
Encryption and secure data storage
Encrypting data in transit between servers and at rest keeps it secure even if someone intercepts it. While many organizations rely on their cloud provider to manage encryption keys, taking more direct control of key management can further strengthen security. Using customer-managed keys or dedicated key management services gives you more visibility and control over who can decrypt your data and reduces the impact if a provider account is compromised.
When properly implemented, modern encryption standards like 256-bit Advanced Encryption Standard (AES) are considered highly secure with current technology. The challenge lies in effectively rotating encryption keys without creating new vulnerabilities.
Learn more: Read our detailed guide on symmetric vs. asymmetric encryption.
Compliance and regulatory challenges
Data security in cloud computing goes beyond protecting company assets. There are also legal, compliance, and industry regulations to consider. Cloud environments often span multiple countries and regulatory zones, which means businesses must navigate a complex web of compliance requirements to avoid fines and reputational damage.
Key cloud compliance standards
Recognized security frameworks dictate the protection and management of data for both cloud providers and their customers. Common examples include:
- International Organization for Standardization (ISO) / International Electrotechnical Commission (IEC) 27001: This defines requirements for implementing, maintaining, and continually improving an information security management system (ISMS) to protect data confidentiality, integrity, and availability.
- System and Organization Controls (SOC) 2: An auditing standard developed by the American Institute of Certified Public Accountants (AICPA). It assesses a company’s controls related to data security, availability, processing integrity, confidentiality, and privacy through an independent auditor’s report that confirms whether those controls are designed and operating effectively.
These frameworks guide how cloud systems are designed, monitored, and audited, but businesses still share responsibility in applying them correctly.
While ISO 27001 isn’t legally required, many customers,especially for software-as-a-service (SaaS), data storage, and analytics services, expect it as proof that security is a priority. SOC 2 plays a similar role, mainly in North America, while ISO 27001 is used globally. Companies serving customers in multiple regions often pursue both certifications, sometimes aligning audits because many of the controls overlap.
Regional requirements
Compliance rules depend on where a company operates and the type of data it handles. Here are a few examples:
- General Data Protection Regulation (GDPR): A data-protection regulation enforced across the European Union. It governs how organizations collect, store, and use personal data of individuals in the EU. Article 32 specifically requires appropriate technical and organizational security measures.
- Health Insurance Portability and Accountability Act (HIPAA): A U.S. federal law that sets standards for protecting sensitive patient health information. It requires covered entities and their business associates (including cloud providers handling medical data) to implement safeguards ensuring confidentiality, integrity, and availability of protected health information.
- Personal Information Protection and Electronic Documents Act (PIPEDA): Canada’s federal privacy law that regulates how private-sector organizations collect, use, and disclose personal information.
- California Consumer Privacy Act (CCPA): A state law in the U.S. that gives California residents control over their personal data and requires businesses to implement data protection measures.
Cloud compliance is an ongoing process. Regulations evolve to meet the latest threats, and businesses need to continuously update their data policies to remain compliant. Understanding data residency requirements is particularly important, as some regulations require data to stay within specific geographic boundaries.
How to address security concerns in cloud computing
Organizations need a comprehensive and flexible strategy that evolves to address new threats and emerging technologies.
Understanding provider vs. customer security responsibilities
A key challenge in cloud adoption is knowing where the provider’s responsibility ends and the customer’s begins. While the cloud provider manages the security of the cloud, the customer is responsible for securing what they store in the cloud.
It's essential users of the cloud effectively handle security on their side: monitoring user access, managing configuration changes, reviewing data interfaces, and testing business continuity plans.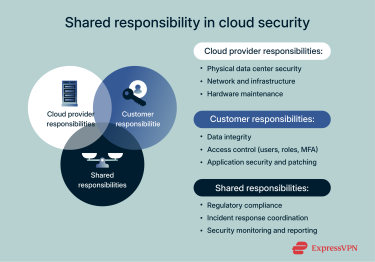
Implementing the zero-trust model
The concept of zero trust is simple: nobody is trusted by default. Every user, device, and connection needs authentication before it can access any cloud resources.
This approach assumes that threats can come from inside or outside the network. Zero-trust cloud security architecture treats every access request as if it comes from an untrusted network, regardless of its actual source. Only once it’s verified can it access the requested data.
Leveraging AI and machine learning for threat detection
Cloud environments generate massive amounts of data, far more than humans can analyze. AI and machine learning (ML) algorithms can be trained to detect anomalies, such as unusual login patterns, data transfers, or changes in settings. These tools help security professionals respond faster to potential threats.
ML models can establish accepted behavioral norms and send alerts when they detect any deviation that might indicate compromise. This way, organizations stay proactive instead of reactive and can stop cloud security threats before they cause any damage.
DevSecOps and continuous security
Development, security, and operations (DevSecOps) integrates security directly into the software development cycle, ensuring that protection is built into every stage, from code design to deployment. By incorporating automated testing, vulnerability scanning, and real-time monitoring, it keeps cloud systems secure even as new features are released. Continuous security also helps organizations maintain compliance as systems evolve.
This approach catches vulnerabilities early in development, when they’re cheaper and easier to fix. It’s built around continuous integration and continuous delivery (CI/CD): a process where code changes are automatically tested, reviewed, and deployed to production in small, frequent updates. By embedding security into CI/CD pipelines, organizations can move faster without sacrificing protection.
Secure access service edge (SASE)
SASE combines networking and security functions into a single cloud-based framework. This can include secure web gateways that filter and inspect web traffic, Firewall-as-a-Service (FWaaS) that provides cloud-based firewall protection, and zero-trust network access (ZTNA) that verifies each user and device before granting access to specific apps. It allows organizations to secure users and data consistently, whether they're working on-site or remotely.
As workforces become more distributed, SASE offers a unified security policy that travels with users regardless of their location or device. It’s essential for organizations with remote teams accessing cloud resources from multiple locations.
Learn more: Read our in-depth guide to cybersecurity, covering its main challenges, business benefits, best practices, and solutions.
Choosing the right cloud security strategy
Building a secure cloud environment starts with choosing the right strategy. Security decisions should balance flexibility, cost, and compliance with clear risk management practices.
Evaluating cloud service providers' security models
Companies need to build a cloud security strategy that fits their specific needs. Before choosing a platform, review its shared responsibility model to understand which security controls the provider manages and which ones fall to you. Verify that the provider uses strong encryption, MFA, and data residency options that follow frameworks such as ISO/IEC 27001 or SOC 2 and any regional requirements.
Reliable providers publish detailed transparency reports and undergo regular third-party security audits. These audits confirm that the provider meets the security standards it claims to uphold.
Questions to ask during vendor assessment
Security should be part of the conversation when evaluating potential providers. Here are some important questions to ask:
- How is customer data encrypted in transit and at rest?
- What procedures are in place for incident response and breach notification?
- Can you choose where your data is stored geographically?
- How are APIs secured and monitored for abuse?
- What tools are available for access control and activity logging?
- How does your shared responsibility model in cloud security work in practice?
- What security certifications do you maintain, and how often are they audited?
Answers to these questions give organizations insights into a cloud provider’s security policies and who is responsible when something goes wrong.
FAQ: Common questions about security concerns in cloud computing
Is using a VPN necessary for cloud access?
For businesses, a cloud VPN is often an important additional layer when employees connect to internal systems, management consoles, or private cloud networks. It encrypts traffic between users or offices and the company’s cloud resources, reducing the risk of interception or credential theft.
How is cloud security different from traditional IT security?
Traditional IT security focuses on protecting systems within a single, contained environment. Cloud security, on the other hand, must protect assets spread across multiple platforms and locations. It relies on shared responsibilities between the provider and the customer, with a greater emphasis on access control, encryption, and continuous monitoring. This dynamic approach helps keep data safe even when it moves across networks.
What compliance laws apply to cloud-stored data?
Compliance requirements depend on where the business operates and what kind of data it stores. Common frameworks include the General Data Protection Regulation (GDPR) in the European Union, the Health Insurance Portability and Accountability Act (HIPAA) in the U.S. healthcare sector, and the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN