The true cost of cyberattacks in 2025 and beyond
Cyberattacks can strike in seconds but leave you paying for months. A ransom note may appear the moment attackers break in, but the real cost, such as instant containment, forensic investigations, legal counsel, crisis-communications support, customer hotlines, regulator filings, and often the ransom itself, can keep invoices rolling in long after the breach.
To take sensible action, you need a clear map of where the money really goes, how those figures are changing, and which proactive moves can protect both your budget and your reputation. That’s the purpose of this article.
What is a cyberattack, and why are costs rising?
Definition and types of cyberattacks
A cyberattack is any malicious attempt to gain unauthorized access to computer systems, networks, or devices to steal data, cause disruption, or inflict damage. This can be as seemingly minor as hijacking your Netflix account or as critical as holding a hospital’s patient records hostage.
In practice, cyberattacks take many forms, including:
| Attack | How it hits you | Why it pays off for criminals |
| Ransomware | Encrypts files and demands ransom, often in crypto, to release them | Fast cash; average payout reached $2 million in 2024 |
| Phishing and business email compromises (BEC) | Emails/texts that trick employees into wiring money or sharing credentials | One click can net six-figure transfers |
| Malware | Installs spyware, keyloggers, or botnets | Steals credentials or uses infected machines to launch spam campaigns |
| Man-in-the-middle (MITM) | Slips between you and a service to intercept and even tamper with your data without you realizing it | Harvest stolen credentials, personal details, or transaction data that they can sell or use to commit fraud |
| Distributed denial-of-service (DDoS) | Floods sites with junk traffic | Knocks stores offline during peak hours; extorts a “turn-off” fee |
| Insider misuse | Employees abusing access or selling data | Harder to spot and often skirts perimeter defenses |
Why the cost of attacks keeps increasing
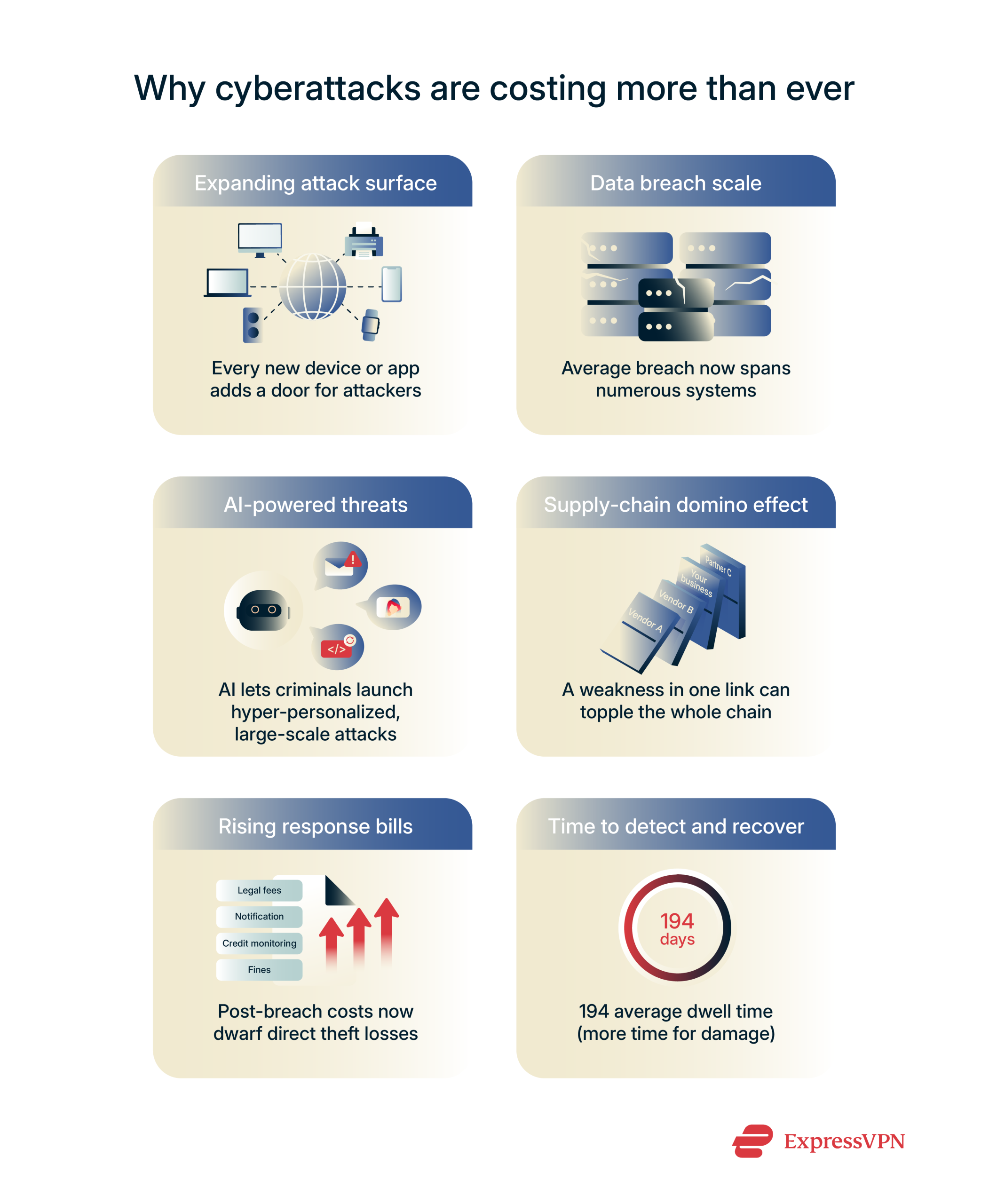 Cyberattacks are more expensive than ever for a few key reasons:
Cyberattacks are more expensive than ever for a few key reasons:
- Increased attack vector: There are so many more interconnected devices today. Every new app, cloud service, or smart device increases the attack surface and the overall risk exposure.
- More data, more damage: Cybercriminals can move laterally across systems in as little as 79 minutes, so by the time you detect and contain an incident, it has often touched dozens of systems, each one adding to your recovery workload.
- More sophisticated threats: Attackers use AI and automation to make attacks more effective, launch attacks on a larger scale, and create highly convincing fraudulent communications. For example, phishing schemes have matured into hyper-personalized “whaling” attacks targeting executives, using AI-generated deepfakes to bypass traditional email filters.
- Interconnected business systems: Businesses increasingly rely on third-party vendors and digital supply chains. A security weakness in one linked entity can be exploited to compromise multiple other organizations, leading to widespread damage.
- Higher post-breach response and compliance costs: Beyond direct losses, organizations face rising expenses for legal counsel, customer notifications, credit monitoring, and regulatory fines. Strict privacy laws like the General Data Protection Regulation (GDPR) can add millions in penalties.
- Extended breach dwell times and recovery efforts: It now takes an average of 194 days to detect a breach, giving attackers more time to steal data and embed ransomware. This drives up both disruption and remediation costs.
Global economic impact of cyberattacks
The global economic impact of cybercrime is substantial and continues to grow. It is estimated to rise from $9.22 trillion in 2024 to $13.82 trillion by 2028. This includes losses from data breaches, ransomware attacks, and other cybercrimes.
The numbers are pretty staggering. In 2015, the global bill for cybercrime was around $3 trillion, so it has more than tripled in less than a decade. It now outstrips the economic damage of natural disasters each year and even surpasses the combined value of the world’s major illicit drug trades. If you treat it as a standalone economy, it would rank third globally, behind only the U.S. and China.
On top of that, intellectual property theft alone costs firms between $225 billion and $600 billion annually in the U.S., undercutting innovation and competitive edge.
Protecting against those losses is driving another spending spree. Cumulative investment in security products and staff is forecast to exceed $1 trillion within the next five years, which is a clear sign of how seriously businesses and governments now take this threat.
Cyberattack statistics and real-world case studies
Cyberattacks aren’t just a headline. They hit your bottom line, your reputation, and your peace of mind. The latest statistics paint a clear picture of these costs, broadly and by organizational scale.
Key cybercrime statistics for 2025
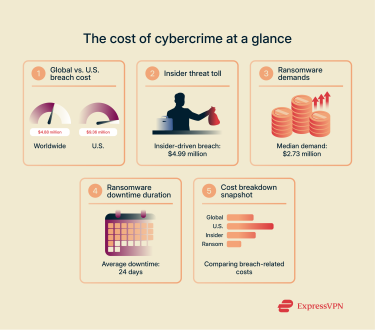 Why should organizations prioritize cybersecurity? The numbers speak for themselves, painting a stark picture of the potential losses:
Why should organizations prioritize cybersecurity? The numbers speak for themselves, painting a stark picture of the potential losses:
💰 Average breach cost (worldwide): $4.88 million
💰 Average breach cost (U.S.): $9.36 million
💰 Insider-driven breach bill: $4.99 million
💰 Median ransom demand: $2.73 million
💰 Average ransomware downtime: 24 days
Average cost of a data breach by business size
💰 Small organizations (fewer than 500 employees): $3.31 million
💰 Mid-sized organizations (500–1,000 employees): $3.29 million
💰 Larger mid-market (1,001–5,000 employees): $4.87 million
Case studies: High-profile attack costs
MGM Resorts
When you look at the MGM Resorts breach in September 2023, the financial impact of cybercrime becomes clear. Threat actors infiltrated reservation systems and casino floors, forcing a multi-day shutdown of key services.
In a U.S. Securities and Exchange Commission (SEC) Form 8-K filing, MGM estimated the incident’s total cost to be over $100 million, plus nearly $10 million spent on one-time consulting and cleanup fees, and millions more in lost revenue during downtime.
MOVEit
The 2023 MOVEit breach highlights the risk in software supply chains. MOVEit, a file transfer platform, was exploited by the Cl0p gang to expose data from over 2,700 organizations and some 95 million individuals. Based on IBM’s average breach cost of $165 per record, this puts the MOVEit incident’s aggregate price tag at around $15.8 billion, covering incident response, legal fees, customer notifications, and more.
Change Healthcare
In another notch on Cl0p’s belt, in mid-2024, Cl0p-linked ransomware hit Change Healthcare, a UnitedHealth Group (UHG) subsidiary. UHG paid a $22 million ransom and has since recorded over $1.6 billion in breach-related costs, including recovery services, vendor support, and emergency capital, bringing its projected total to about $2.45 billion.
Marks & Spencer
Over Easter 2025, retailer Marks & Spencer’s systems were hit via a third-party supplier breach attributed to the Scattered Spider group. Online ordering and app payments were suspended for weeks. In its May 2025 trading update, Marks & Spencer put the total cost, including lost sales, remediation, and insurance shortfalls, at around £300 million.
Who is most at risk?
1. Healthcare and financial services
Healthcare remains the costliest sector when breaches occur. In 2024, the average healthcare breach cost was $9.77 million, driven by lengthy patient-safety investigations, regulatory fines, and steep remediation expenses. The Change Healthcare incident illustrates this danger.
Financial services also face above-average losses. Firms in that industry now spend about $6.08 million per breach as they juggle regulatory penalties, customer litigation, and fraud mitigation.
2. Manufacturing and infrastructure
Disruption to physical operations magnifies costs in manufacturing and critical-service sectors. The industrial average breach cost rose to $5.56 million in 2024, an 18% jump year-over-year, with unplanned downtime alone running as high as $125,000 per hour.
Utilities are especially vulnerable: when Southern Water in the U.K. fell victim to Black Basta ransomware, it incurred direct containment and restoration expenses of £4.5 million (about $5.7 million).
3. Small businesses and startups
In 2023, organizations with fewer than 500 employees faced an average breach cost of $3.31 million. One recent analysis found that 75% of the increase in average breach costs was due to incident response, legal fees, and restoration efforts.
Small businesses present an attractive target to cybercriminals, as they tend to have weaker security measures than larger enterprises. And a successful attack can force cuts to growth initiatives, stretch already limited resources, and, in some cases, jeopardize the business’s survival.
4. High-net-worth individuals and executives
Privileged roles bring deep pockets and, unfortunately, juicy targets. BEC scams now account for billions in annual losses globally, with U.S. businesses reporting nearly $2.90 billion in BEC-related wire-transfer fraud in 2023 alone.
Attackers craft highly personalized spear-phishing campaigns against executives, often extracting six- or seven-figure payments before detection. In one high-profile BEC event, a Luxembourg chemical firm disclosed an SEC filing showing $60 million lost in a single wire fraud scheme.
Prevention vs. recovery: Where does the money go?
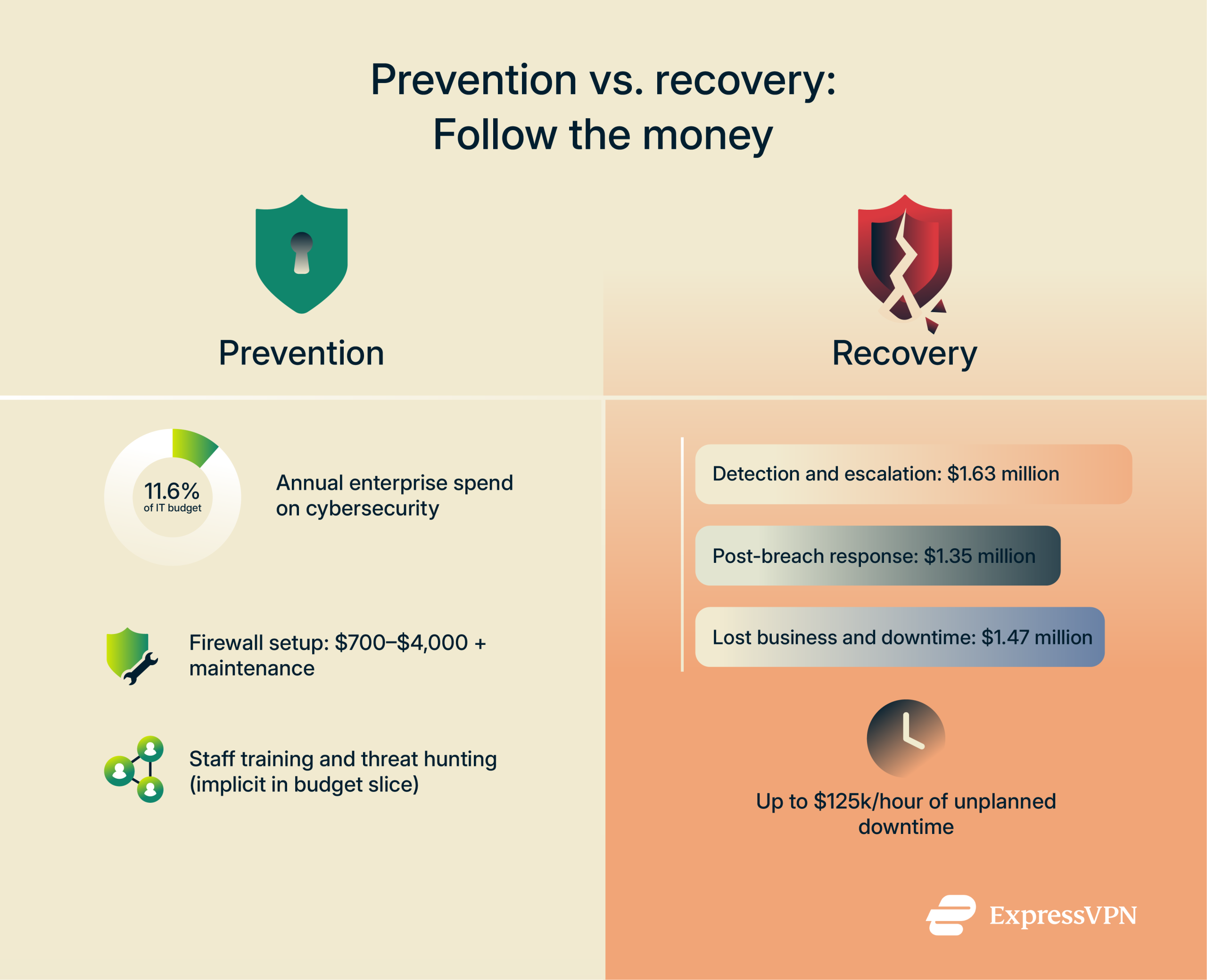
Cost of prevention
Before an incident ever occurs, organizations invest in people, processes, and technology to keep attackers at bay. Research shows that large enterprises, on average, allocate around 11.6% of their IT budget to cybersecurity.
This often comes to several million dollars annually, funding activities such as firewall and intrusion-prevention deployments, endpoint protection, threat hunting, and staff training. For example, a one-off firewall configuration can run between $700 and $4,000, with ongoing maintenance costs on top.
Cost of recovery
When defenses fail, recovery costs from cyberattacks mount quickly. On average, it can come to:
- Detection and escalation: $1.63 million, covering forensic investigations and breach notification processes.
- Post-breach response: $1.35 million for call center setup, credit monitoring, and regulatory fines.
- Lost business: $1.47 million, reflecting downtime, customer churn, and reputational impact. Unplanned downtime alone can cost industrial firms as much as $125,000 per hour, and legal fees or class-action settlements can add millions more.
Why prevention is the more cost-effective strategy
IBM’s 2024 Cost of a Data Breach Report found that companies that invest extensively in security AI and automation faced an average breach cost of $3.84 million in 2024, while those that used none at all had an average breach cost of $5.72 million. In other words, security automation can reduce breach costs by an average of $1.88 million per incident, shrinking the recovery bill significantly.
Even modest prevention outlays, like multilayered endpoint protection or regular staff training, cost a fraction of the price tag associated with legal liabilities, regulatory sanctions, and prolonged downtime.
By shifting spending from reacting to attacks toward thwarting them, organizations not only save money but also limit operational disruption and protect their reputation.
How are governments and businesses fighting cybercrime?
Cybersecurity legislation and global coordination
Regulators worldwide have ramped up rules to raise baseline defenses and support cross-border collaboration. In the European Union, the Network and Information Security (NIS2) Directive and the proposed Cyber Resilience Act impose mandatory security measures on essential operators, like banks, hospitals, utilities, and digital service providers, with penalties reaching up to €10 million or 2% of global turnover for non-compliance.
In the United States, the Cybersecurity and Infrastructure Security Agency (CISA)’s International Strategic Plan 2025–2026 prioritizes sharing threat intelligence and harmonizing standards across allies to protect critical infrastructure, from power grids to healthcare networks.
Cyber insurance: Does it help or hurt?
Cyber insurance can cover costs after a breach, including legal fees, forensic investigations, and even regulatory fines. It gives you a financial backstop if your defenses fail. Yet it also has limits:
Pros:
- Offsets unexpected expenses such as breach notification and customer credit monitoring.
- Encourages you to adopt basic security controls to qualify for coverage.
- Offers access to vetted incident response firms and legal counsel.
Cons:
- Premiums rise if you’ve filed multiple claims or lack strong security measures.
- Policies often exclude social engineering, insider threats, and fines in certain industries.
- Claims can be delayed or denied if you miss a policy requirement, like timely patching or employee training.
Treat cyber insurance as one layer in your defense, not a replacement for good practice. You still need to lock down accounts with multi-factor authentication (MFA), encrypt data in transit with a virtual private network (VPN), and train your team on how to detect a phishing attempt. In the event of a breach, insurance kicks in, but prevention and rapid response remain your best savings.
The rise of AI in threat detection
AI and machine learning are transforming how organizations spot and stop attacks. Instead of relying on static signature databases, AI-driven tools analyze behavior across networks and endpoints in real time. That means they can flag unusual login patterns, data transfers, or lateral movement that conventional defenses might miss.
AI systems continuously learn from new threat data, trimming false positives and sharpening alerts. When a novel malware strain appears, AI models can detect its “DNA” by comparing code patterns and execution behavior against millions of known samples. This accelerates response; security teams see emerging threats within minutes instead of days.
That said, AI isn’t a silver bullet. Attackers still have their own techniques to fool models, and overreliance on automation can breed complacency. Human expertise is still one of the best ways to verify alerts, tune rules, and investigate complex incidents. For the best protection, combine AI’s speed with your security team’s judgment.
How to protect yourself and your business from cyberattacks
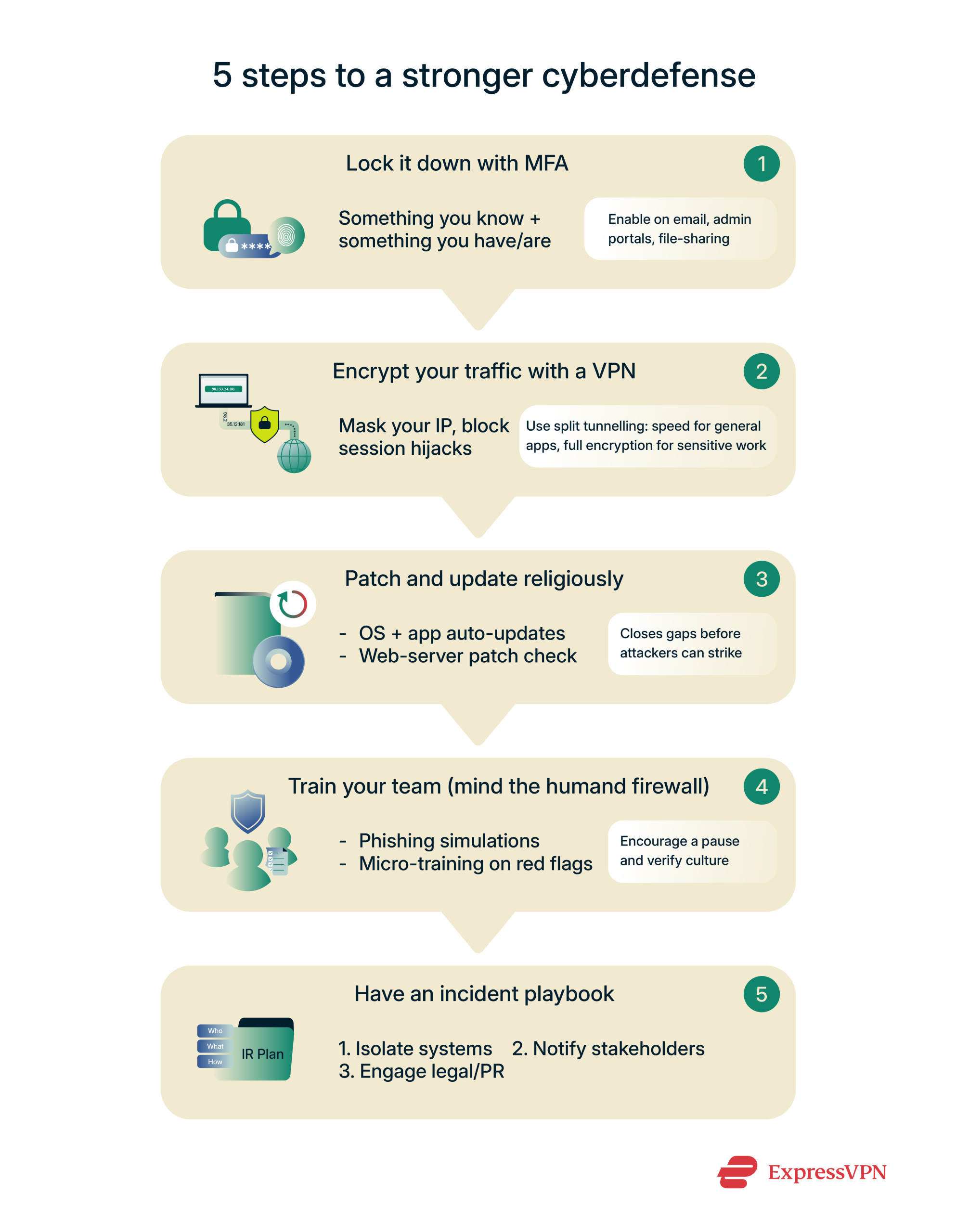 Protecting yourself and your business from cyberattacks takes more than a single tool or policy; it involves building habits that keep threats at bay. Here are five steps to take.
Protecting yourself and your business from cyberattacks takes more than a single tool or policy; it involves building habits that keep threats at bay. Here are five steps to take.
1. Use multi-factor authentication (MFA)
Ensure your team uses strong, unique passwords for every account and stores these in a secure password manager. Then, layer on MFA, which is authentication via something you know (your password), plus something you have (a one-time code on your phone, a hardware key) or something you are (a fingerprint).
Even if a cybercriminal steals a password, they can’t log in without that second factor. So make sure to enable MFA on every account that supports it, including email, file-sharing services, and admin portals, so you’re not a single data breach away from a full compromise.
2. Consider using a virtual private network (VPN)
A VPN encrypts every data packet you send or receive, making it unreadable to attackers on the same network. By masking your IP address, you also block session hijacking attempts and give your zero-trust policies an extra safeguard. Some VPNs also offer split tunneling, which lets you keep day-to-day apps on your local connection while routing sensitive work traffic through the VPN.
3. Keep software updated and patched
Attackers exploit known vulnerabilities in outdated software. Make it a habit to install operating-system updates, patch your web server, and update any third-party applications as soon as patches arrive. Turn on automatic updates where possible: this closes gaps before attackers can spot them. Regular patching shrinks the window of opportunity for malware, ransomware, and other threats.
4. Educate employees to prevent human error
Your team is the best yet most vulnerable line of defense. Run short, frequent training sessions on phishing red flags, safe browsing habits, and proper file-sharing protocols. Simulate phishing emails to see who needs a quick refresher. Reinforce a culture where anyone can pause and verify a suspicious link or attachment without fear of blame. Informed employees catch attempts before they turn into breaches.
5. Develop an incident response plan
When an attack happens, speed matters. Create a clear playbook that spells out who to call, which systems to isolate, and how to communicate internally and externally. Test your plan with tabletop exercises and update it after each drill or real incident. Knowing exactly what to do (and who’s in charge) cuts downtime, limits damage, and gets you back to business faster.
FAQ: Common questions about the cost of cyberattacks
What is the average cost of a cyberattack?
Roughly $4.88 million per breach worldwide, ballooning to over $9 million for U.S. organizations.
How can small businesses afford protection?
Start with the basics: built-in firewalls, multi-factor authentication (MFA), regular software updates, and a reliable VPN. Outsource monitoring to an affordable managed security provider and consider a reasonably priced cyber-insurance policy.
Is cyber insurance worth it?
If a breach would sink cash reserves, yes. Just read exclusions carefully and make sure to meet the insurer’s security prerequisites around multi-factor authentication (MFA), backups, and documented policies. Insurance won’t rebuild trust, but it pays the hefty invoices that follow an incident.
Which industries lose the most to cybercrime?
According to the IBM X-Force Threat Intelligence Index 2025, manufacturing is the most targeted industry, accounting for 26% of all attacks. However, healthcare tops per-incident costs (~$10 million). Finance follows at roughly $6 million, then manufacturing, energy, and tech hover near $5–6 million. Public sector breaches tend to cost less per incident but still disrupt vital services.
How can I reduce my exposure to cyber threats?
There are a number of ways: use unique passwords with a manager, lock every key account with multi-factor authentication (MFA), patch software promptly, back up critical files offline, train staff to spot scams, and secure all internet traffic with a reputable VPN, especially on public networks or when handling sensitive data.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN