What is a keylogger, and how does it work?

It’s 1976. The Cold War. An American diplomat stationed at the U.S. embassy in Moscow arrives at work Monday morning. Sitting down at his desk, he types up his reports on his IBM Selectric typewriter. He thinks he’s secure. Little does he know that every word he’s typing is being recorded.
His typewriter had been bugged by the Soviets using the world’s first ever keylogger: a miniaturized set of circuits crammed into a metal bar that ran along the typewriter. It was hidden from view and could record every key press and transmit the data in real time. It would take eight years for the Americans to discover this.
These days, however, keyloggers are disconcertingly common. In fact, recent studies have found thousands of popular websites unintentionally recording phrases typed into online forms before the user even hits “Submit.” In other cases, keyloggers are used as spyware for companies to monitor employees, stalkers to spy on exes, or cybercriminals to steal identities.
Today’s keyloggers are more advanced than those of decades gone by, with both physical and digital versions in usage. They can be used in various ways, with potentially grave consequences for their unwitting victims. This guide answers the questions of what a keylogger is, how it works, and how you can detect and defend yourself against them.
What is a keylogger?
Imagine a device or program that is capable of tracking every single key you press on your keyboard, creating a log of all that information, and sending it off to someone else, like your boss, your ex, or even a complete stranger.
That, in a nutshell, is what a keylogger is. While they vary in complexity and design, their main function is logging keystrokes, and they can be used both maliciously and for legal, consensual reasons, too (more on that below).
Types of keyloggers
We can divide keyloggers into two main types: software-based and hardware-based. While both carry out the same core function and pose a threat to unsuspecting victims, they differ greatly in terms of how they’re installed and accessed.
Software-based keyloggers
Software keyloggers are the most common variety in use today. They take the form of computer programs, often surreptitiously installed on target devices. Once active, those programs can track and record keystroke data. They also often have the ability to transfer that data to a criminal, who could be somewhere nearby or on the other side of the world.
Many software-based keyloggers also fall into the category of remote keyloggers, meaning that they can be installed and accessed remotely, without the need for close contact with the target device.
Mobile keyloggers also tend to be software-based, too. Hardware-based keyloggers don’t tend to work on these smaller devices, since there’s less space in which to conceal them.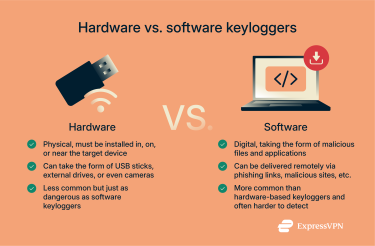
Hardware-based keyloggers
Hardware-based keyloggers are physical devices that are typically attached to or concealed within a computer to monitor keystrokes directly. They often take the form of seemingly simple, innocuous accessories, like a USB stick, or may even be concealed within the keyboard, a cable, or the computer case itself.
There are even cases in which physical or hardware-based keyloggers aren’t directly connected to the victim’s device. Criminals may, for instance, set up a secret webcam in a public location, like a library or café, and use that to record and monitor a user’s keystrokes and other computer activities.
It’s worth noting, too, that criminals may use a combination of physical and software-based keylogger attacks. They might deploy a USB drive as a Trojan horse, for example, using it to deliver a keylogger program onto a device. Then, even if the drive is detected and removed, the keylogger will still remain hidden away in the system files.
How do keyloggers work?
Tapping keys on a keyboard is how we essentially “talk” to our computers and issue commands. Typically, that conversation between you and your computer should be private, but keyloggers are almost like nosy neighbors, hiding nearby, listening in to everything you say, and noting it all down.
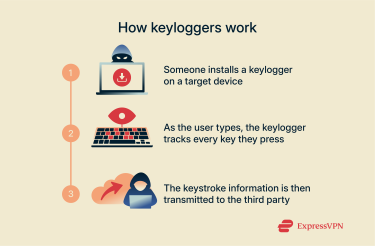
Common delivery methods
Cybercriminals use various methods to get keyloggers onto their victims’ devices.
In the case of hardware-based keyloggers, they often need to have physical access to your device. They might wait until their victim leaves a device unattended and then take that opportunity to install their keylogger or disguise keyloggers as innocent accessories that they could then send, sell, or leave lying around in the hopes that someone tries to use it.
For software-based keyloggers, some of the most common delivery methods include:
- Phishing emails: Phishing is the most common form of cyberattack, with literally billions of phishing emails sent out daily. These emails may appear safe and legitimate at first but often contain malicious links or attachments. If clicked, those links or files may trigger the installation of keylogger software onto the victim’s device.
- Drive-by downloads: A drive-by download is when a keylogger is quickly and sneakily installed onto a device without the owner’s awareness. It often occurs when a user clicks a link or visits a malicious site, and the keylogger files automatically download and install without the user being asked for any kind of confirmation.
- Trojan horse malware: A Trojan horse is a file or application that seems perfectly innocent and safe at first glance but has malicious files or code concealed within. Criminals can disguise keylogger software in this way, tricking users into opening and installing it.
There are also documented cases of major tech brands selling computers and laptops with keylogger software mistakenly built in. So even if you follow cybersecurity best practices and avoid clicking malicious links and visiting shady sites, you could still be at risk.
Data collection and transmission
Once installed, all keyloggers, whether they’re hardware- or software-based, have the same basic functionality: they collect a record of which individual keys you press and in which order, and some can even figure out how hard you press each key and how long you hold it down for, too.
They save all that information in a tiny file on your device or, in the case of hardware loggers, in their own internal memory. They can then either transmit the information digitally to someone else, or a criminal may have to physically retrieve their logger to access the data it has collected.
Uses of keyloggers
Many people associate the concept of keyloggers with illegal activities, like hackers trying to steal your passwords and track your every online action. While that is true to an extent, and keyloggers can be used in very malicious ways, they also have more legitimate applications. 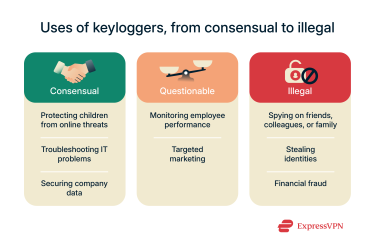 Below, we’ll explore some examples in the legal, questionable, and criminal categories.
Below, we’ll explore some examples in the legal, questionable, and criminal categories.
Legal consensual use
Sometimes, users may knowingly accept to have keyloggers installed on their devices for the following purposes:
- Parental supervision: From cyberbullies to groomers and exposure to explicit content, kids today are exposed to all sorts of online dangers. Parents may choose to install a keylogger on their child’s computer or phone to monitor their internet usage and receive alerts if the software detects any concerning words or phrases.
- IT troubleshooting: IT technicians may use keylogger software when attempting to troubleshoot and resolve problems on a device. For example, a keylogger might help IT pros record a user’s keystrokes when they attempt to reproduce a system or software bug, helping them understand what triggers the bug and how to fix it.
- Company security: Companies that handle a lot of sensitive data or are at high risk of cyberattacks and data breaches might use keyloggers as part of their cybersecurity strategy. They could set up their keyloggers to only track specific phrases or patterns of behavior that might be linked with employee sabotage or data leaks, for example.
Questionable or ethically ambiguous use
In other cases, use of keyloggers may begin to stray into more ethically ambiguous territory, such as:
- Monitoring employees: Some companies make use of keylogger software to keep tabs on their employees. While the practice is legal in most countries (usually with some restrictions, such as the obligation to notify the employee that their keystrokes are being logged), employees themselves largely view it as a breach of privacy.
- Marketing purposes: Many websites in both the U.S. and the EU have been found to collect users’ email addresses without their consent. This data is then used to bombard people with targeted ads. However, governments have been clamping down on these practices through privacy regulations.
Criminal use of keyloggers
There are also entirely malicious and illegal uses of keyloggers, for purposes like:
- Identity theft: Cybercriminals could use keyloggers to effectively steal a large part of a person’s digital identity. They could track every username and password their victim types, for example, and then secretly gain access to their accounts or sell their personal information and digital credentials on the darkweb to other criminals.
- Spying on friends and family: People might also abuse keylogger technology to spy on those they know. They could illicitly install a physical or digital keylogger on a friend or family member’s device and then monitor their online activities, seeing every word they type, every website they visit, and every message they send.
- Financial theft and fraud: Criminals can also use keyloggers for financial gain and fraudulent activity. They can use them to steal a victim’s bank login details, credit card numbers, or crypto wallet credentials, for instance, and use that information to make payments of their own.
How to detect a keylogger
By their very nature, keyloggers are sneaky and tricky to detect, but there are certain tools you can use and warning signs you can watch out for.
Common warning signs
A keylogger may affect your device’s performance in the following ways:
- Typing delays and freezes: A keylogger activates every time you press a key, and that can cause a slight but sometimes noticeable impact on performance. You may notice, for example, when typing that there’s a slight delay or freeze between pressing the key and the resulting letter or action occurring on the screen.
- Unknown background processes: Keyloggers operate stealthily in the background as you go about your usual tasks, but you can often still spot them by looking at a list of active processes on your computer in the Task Manager on Windows (CTRL + Shift + ESC) or the Activity Monitor on a Mac (Command + Spacebar).
- Browser or app hijacking: Keyloggers may be combined with other malicious tools, like browser or app hijackers, which can allow cybercriminals to change your browser or application settings remotely. Keep a close eye on your most-used apps and your internet browser for any changes you don’t remember making.
- Mobile device signs: On a mobile device, signs of a keylogger’s presence include the device getting unusually hot due to extra background processes running when you type, as well as the battery draining much more quickly than normal. You might also notice app icons you don’t recognize, and general performance may be slow and sluggish.
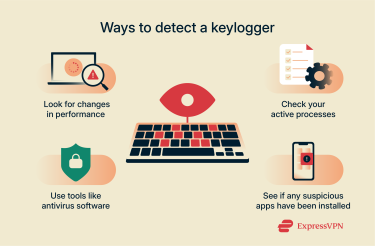
Tools to detect keyloggers
While keyloggers are often hard to spot, various tools can help you identify and eliminate them. These include:
- Anti-malware programs: An antivirus may be able to detect and quarantine or remove keyloggers from your device. Just make sure to use a reputable program for the best results, and opt for those that have anti-rootkit capabilities, as the sneakiest sorts of keylogger software come in rootkit form to affect the deepest levels of your system.
- Lists of installed apps and extensions: Another simple way to check for signs of keyloggers on any device is to check the list of installed apps and browser extensions. You may notice apps/extensions you don’t recognize in the list, and you can research them to learn more about them. They may be keyloggers in disguise.
- Physical inspections: If you have any suspicion of hardware-based keyloggers on your device, a visual inspection is worth a try. You can inspect your device yourself or take it to a trusted tech expert who can safely open it up and take a close look at internal components for any signs of tampering.
What to do if you detect or suspect a keylogger
Detection is only part of the solution when it comes to dealing with malicious devices and software, like keyloggers. Even if you identify a keylogger using any of the methods listed above, the criminal who installed it may already have access to your data. As such, it’s important to take the appropriate next steps, which include:
- Disconnecting your device from the internet so the keylogger can no longer transmit any data to any third parties.
- Running a full system scan of your device to find any traces of keylogger software and remove them with the aid of your anti-malware program. You may also need to manually uninstall or remove offending app(s) and potentially carry out a complete factory reset of your device to get rid of any traces of keylogger software.
- Updating and changing your login credentials for any accounts and platforms that could be at risk, especially the likes of online bank accounts. Enable two-factor authentication (2FA) on those accounts if possible, too, for extra security. If you believe any accounts are compromised, you may also want to inform the relevant platforms, like your bank.
- Reporting the situation to relevant authorities and professionals. In the U.S., you can report cybercrimes like keyloggers to the Internet Crime Complaint Center (IC3) or the Federal Trade Commission (FTC), as well as local law enforcement, who may also be able to advise on the next best steps for you to follow.
How to protect yourself against keyloggers
Detecting and dealing with keyloggers can be immensely difficult, and it’s much simpler to take a proactive, preventative approach instead, using the following methods and solutions to safeguard your device from possible attacks.
Antivirus software
This won’t work against physical keyloggers, but antivirus programs are often quite effective at not just rooting out software-based keyloggers but also preventing them from infecting your device in the first place.
Safe browsing habits
As explained earlier, cybercriminals often deploy keyloggers and other kinds of malicious software via phishing links and fake websites. Practicing safe browsing habits, such as:
- Never click on suspicious links, especially in emails from strangers or suspicious sources.
- Consider switching to a more secure browser, like Tor or Brave, and use secure browser extensions where possible.
- Make use of helpful security tools. ExpressVPN's Threat Manager, for example, is a tool that comes for free with every ExpressVPN subscription, and it minimizes your risk of inadvertently downloading any unsafe files or malicious applications by blocking known unsafe sites.
Physical device security
The risk of physical keyloggers is generally much lower than software-based ones, as they’re more difficult for criminals to set up. However, it’s still important to never leave your device unattended in public places, from cafés to airports, schools, and workplaces. Additionally, be cautious about using any pieces of hardware you don’t know the origins of, like random USB sticks or external drives.
Two-factor authentication (2FA) and password managers
These tools won’t necessarily guard you against keyloggers, but they will help mitigate any consequences if one ends up on your device.
- 2FA provides an extra layer of security to your accounts, so even if someone knows your password, they still won’t be able to log in and steal your identity.
- Password managers like ExpressVPN Keys store all your password data and use it to autofill login forms, so you won’t need to type out passwords when accessing accounts. That makes it much harder for any criminals with keyloggers to steal your credentials.
FAQ: Common questions about keyloggers
Can a keylogger be detected easily?
No, keyloggers can be quite difficult to detect, both in physical and digital formats. Visual inspections of devices may help in spotting physical keyloggers, and anti-malware programs can aid in identifying software keyloggers. Users can also watch for signs that a keylogger might be in operation, like slow computer performance or random crashes and freezes.
What is an example of a keylogger?
Keyloggers come in two distinct forms: hardware and software. An example of a hardware keylogger might be a malicious USB drive attached to a PC that tracks and transmits keystrokes. An example of a software keylogger is an API-level program that captures signals sent from the keyboard, effectively recording every single key the user presses.
Are keyloggers illegal?
Not necessarily. Someone could install a keylogger on their own device without breaking the law or set up a keylogger on another user’s device with their consent, perfectly legally. However, use of keyloggers typically becomes illegal if they are installed without the device owner’s consent or knowledge, as this breaches various privacy laws and regulations, like the General Data Protection Regulation (GDPR). However, it’s worth remembering that laws may vary around the world.
How do I know if I am infected with keylogging malware?
Unfortunately, because of their sneaky nature, many victims don’t know that their device has a keylogger installed. Nevertheless, you may be able to spot certain signs of a keylogger’s presence, like slow performance and random crashes. You can also use antivirus software to scan your system and remove software-based keylogging threats.
What is the difference between a keylogger and spyware?
Spyware is a broad term, applying to all malicious software that secretly gathers data about a user’s computer activities without their consent. Keyloggers are effectively a specific sort of spyware, able to capture and log individual keystrokes and transmit that information to a third party, though they are not always used for malicious purposes.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN