What is wardriving, and how does a VPN help protect you?

Wi-Fi is very convenient, but it’s also very much public. This comes with inherent vulnerabilities. Malicious actors use a practice called wardriving to silently gather data about nearby wireless networks. Depending on what they find, they can use this information for nefarious purposes.
In this article, we’ll break down what wardriving is, how it works, whether it’s legal, and what you can do to protect yourself (hint: using a VPN won’t hurt).
What is wardriving?
Wardriving is a form of wireless network scanning. It involves searching for Wi-Fi networks using specialized software and hardware while driving around in a vehicle.
While it’s most commonly referred to as wardriving, if performed while walking or via other methods of transport, it may be called warwalking, warbiking, etc.
The term was popularized by WarGames, a 1983 movie where the protagonist engages in a similar, phone-based technique called wardialing.
What is the purpose of wardriving?
Wireless internet scanning is undertaken for a variety of reasons. Some are harmless, but wardriving is often unambiguously malicious.
Benign wardriving involves logging information about nearby Wi-Fi networks without trying to connect to or interfere with them. People might do this for security research, network mapping, or simply out of curiosity. For example, a wardriver might be out to gauge local encryption standards or gather data for the purposes of urban planning or academic research.
On the other end of the spectrum, malicious wardrivers collect data about Wi-Fi networks to identify poorly secured Wi-Fi networks that can be exploited. This is also referred to as network reconnaissance. In niche cases, wardrivers can even harvest email addresses and passwords from unsuspecting victims.
What data is collected during wardriving?
Here are some types of data that can be collected through wardriving:
- Network name (or Service Set Identifier, SSID): This could be anything from “HomeWiFi” to “CoffeeShopGuest.”
- Usernames and passwords: By spoofing a certain type of network configuration, a wardriver could harvest the usernames and passwords of those who regularly connect to the network.
- Basic Service Set Identifier (BSSID) or Media Access Control (MAC) address: These are unique numbers assigned to each access point that help identify the device.
- Location of the Wi-Fi access point: This provides information about the physical location of the device broadcasting the signal.
- Security protocols: This includes information about how the network is protected, including what encryption it uses.
- Signal strength: Measures the power of the signal from the wardriver’s location.
How does wardriving work?
 Wardriving works because Wi-Fi signals are designed to be discoverable. They’re constantly broadcasting their presence to make it easy for users to connect. This means hosts are constantly sharing bits of information. Anyone nearby can read these signals. Specialized software is needed to harvest and process this data en masse, but practically any device can do the trick.
Wardriving works because Wi-Fi signals are designed to be discoverable. They’re constantly broadcasting their presence to make it easy for users to connect. This means hosts are constantly sharing bits of information. Anyone nearby can read these signals. Specialized software is needed to harvest and process this data en masse, but practically any device can do the trick.
Below is a look at what goes on in a typical wardriving excursion.
Scanning wireless networks
The first step in wardriving is detecting nearby wireless networks. This is done using a portable device (typically a laptop) equipped with Wi-Fi connectivity and running wireless local area network (WLAN) monitoring software (Kismet is a popular pick).
GPS and signal mapping
Many wardrivers pair their scanning setup with a GPS receiver. This allows them to build maps that show the geographic distribution of Wi-Fi networks, approximate router locations, and signal strength coverage zones. This is called signal strength mapping.
Data logging and storage
Once networks are scanned and location data is recorded, wardrivers store this data for later use, either locally or on public databases like WiGLE.
Wardriving tools and technology
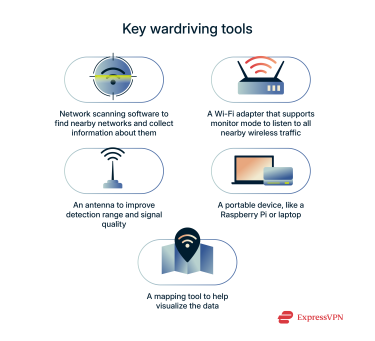
What software is used for wardriving
Kismet is one of the most popular tools for wardriving. It’s a scanner that detects nearby wireless networks by listening to the signals they broadcast. It automatically logs network names, MAC addresses, security settings, signal strengths, and more. When paired with a GPS, it can also be used to create detailed maps of local Wi-Fi networks.
One reason Kismet is so popular is that it’s a passive Wi-Fi sniffing tool, meaning it only collects data that Wi-Fi networks are already broadcasting publicly. This makes it safer from a legal and ethical standpoint than active scanning tools that attempt to connect to networks or send out probe requests.
Other tools that perform a similar function to Kismet include NetStumbler (a bit outdated), inSSIDer, airodump-ng, and Acrylic Wi-Fi.
What Wi-Fi adapters and antennas do wardrivers use?
To get the most data, wardrivers need special Wi-Fi adapters that support advanced features. Most importantly, they need to support monitor mode, a feature that allows the device to listen to all wireless traffic nearby (and not just the networks it’s connected to).
Wardrivers performing penetration testing will also want an adapter that supports packet injection, which is the ability to send custom data packets to a wireless network to test for vulnerabilities. Keep in mind that this is an active network interaction and is usually illegal when done without permission.
To improve range and signal quality over what you get with any old laptop, external antennas are required. Omnidirectional antennas are preferred because they can pick up signals from all directions.
However, those conducting penetration testing or targeting specific networks may use directional antennas, which focus the signal in one direction to achieve a longer range and better accuracy.
What devices are best for wardriving?
Portability is obviously a big factor. Beyond that, a wardriving device must also have a Wi-Fi adapter capable of monitor mode, support the wardriver’s favored software, and have a GPS chip for mapping purposes.
Raspberry Pi rigs are ideal because they're lightweight and highly customizable. But a laptop running Linux is another flexible and powerful option, especially for users who want a full-featured setup with a larger screen and more processing power. Even if the native network card doesn’t naturally support monitor mode, there are plenty of USB adapters that do.
What mapping tools are used in wardriving?
Mapping tools help wardrivers visualize the location and coverage of nearby Wi-Fi networks. For example, GPSMap, which comes bundled with Kismet, allows users to match wireless network data with GPS coordinates in real time.
Many wardrivers also upload the data they collect to WiGLE, an online platform that aggregates and displays wireless network information from around the world as interactive maps.
How unauthorized users exploit open networks
Once someone performing malicious wardriving finds an open network (a network with no encryption or password protection), they can exploit it in several ways:
- Spying and stealing personal information: A skilled cybercriminal can effectively ‘listen in’ on the data users send and receive, including login credentials, emails, or web activity.
- Launching man-in-the-middle (MITM) attacks: In this kind of attack, a threat actor intercepts and modifies the data going between you and a server. This allows them to redirect you to a fake login page, insert malicious code, or trick you into downloading harmful software.
- Piggybacking: Cybercriminals can use victims’ Wi-Fi to download illegal content, send spam, or launch further cyberattacks. Troublingly, this activity will get traced back to the network owner rather than the real culprit.
- Gaining deeper access: If a network or router is poorly secured, a talented attacker can access shared folders, devices like printers or security cameras, or even log into the router itself. From there, they could change settings, install backdoors, or monitor everything happening on the network.
Examples and real-world cases of wardriving
Wardriving can take many forms, some innocent, others deeply concerning. To complete the picture of what wardriving really is, it helps to review some concrete examples.
Theoretical wardriving scenarios
For many people, cybersecurity is something of a hobby. Imagine a tech geek with a particular interest in Wi-Fi security using wardriving to map out Wi-Fi coverage in a public area. Perhaps they’re working on a side hustle and aim to help local businesses improve networks with poor signal strength.
An example of malicious wardriving is a threat actor driving through a neighborhood looking for an unsecured home router that they can connect to. This would allow them to monitor network traffic and potentially obtain sensitive personal information.
More worryingly, it’s possible for a wardriver to harvest usernames and even passwords of specific sets of victims. This is possible thanks to the existence of large organizations (some international in scope) that host webs of wireless networks. Accredited users need to provide authentication to connect to one of the organization’s Wi-Fi hubs. Often, this means providing an email and password associated with the organization (like a workplace or university).
By spoofing such a network and driving around, a wardriver could gather this kind of sensitive information as victims’ devices attempt to automatically connect to the spoofed network. If the username and password required to connect are tied to other accounts (as they usually are), this is obviously a huge potential risk.
Notable wardriving incidents
A high-profile wardriving-related incident occurred in 2010, when it was revealed that Google’s Street View cars were collecting not only publicly available information, such as SSIDs and MAC addresses, but also approximately 600 GB of personal data from unsecured Wi-Fi networks.
It’s worth noting that Google did not intend to collect this information. That said, it included private data like emails, passwords, and files.
Another notable incident was the TJX data breach in 2007. The hackers utilized wardriving to identify poorly secured Wi-Fi networks at two Marshalls stores and exploited these vulnerabilities to gain access to more privileged internal systems. Ultimately, this allowed them to steal millions of customers’ personal information (including credit card numbers).
Is wardriving illegal?
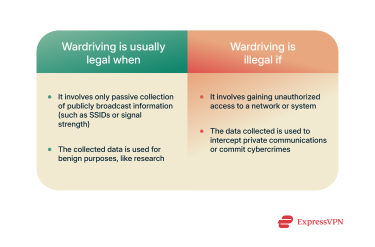
Legal vs. illegal use
In most countries, wardriving isn’t explicitly illegal. This is because, strictly speaking, wardriving is just passively collecting public information. It all depends on which of the many purposes lies behind the wardriver's actions. Using wardriving data to break into a network or intercept data is illegal almost everywhere, whereas using the same data to create a signal map usually isn’t.
Laws by country or region
Laws concerning wardriving vary between countries, so it’s best to familiarize yourself with local laws and regulations before considering taking up the hobby.
In the U.S., wardriving isn’t explicitly illegal, so long as you aren’t using that data to gain unauthorized access to a computer system or network. But in countries with stricter cybercrime laws, like Germany or Singapore, wardriving may fall under a legal grey area or be outright illegal.
Ethical hacking vs. malicious intent
In most jurisdictions, determining whether wardriving is legal or not will generally come down to how the information collected is intended to be used. Wardriving is frequently a prelude to crime, like cyber fraud or cyberstalking.
With malicious intent, threat actors use wardriving to identify weak or misconfigured networks that they can take advantage of to steal personal data, intercept communications, inject malware, etc. In any of these cases, the wardriver is almost certainly breaking the law.
But wardriving can also be done with good intentions. For example, security researchers often use wardriving techniques to identify vulnerabilities in wireless networks so that they can be fixed, kind of like white hat hackers.
How can you protect yourself against wardriving?
There are steps you can take to prevent most potential wardrivers from gaining sensitive information about your network. Fortunately, these are all easy enough to implement.
Use a VPN router or encrypted tunnel
Installing a VPN on your router encrypts traffic across your entire network and hides your devices’ IP addresses. This makes your data unreadable to anyone who might intercept it and protects you from tracking.
Most VPNs can’t be installed on routers. Some can, but the process generally requires a degree of expertise. ExpressVPN, on the other hand, works great on routers. There’s even a router called Aircove that comes with ExpressVPN pre-installed and pre-configured; no manual setup is required.
Update router firmware and set strong passwords
If your router’s firmware is outdated, it may contain security vulnerabilities that malicious wardrivers can exploit. Update your firmware regularly to ensure that you have the latest protections.
It’s also important to set strong passwords, both for your Wi-Fi password and your router’s admin password (used to manage your router's settings). Many people never change their router’s admin password, which is a major security risk.
A strong password should be unique, at least 12 characters long, and contain a mix of letters, numbers, and symbols. You should also avoid common words and phrases. A good password manager, like ExpressVPN Keys, makes it easy to create strong passwords and pull them up whenever you need them.
Enable WPA3 or the highest security protocol
Wi-Fi Protected Access 3 (WPA3) is currently the most secure encryption protocol available for Wi-Fi networks. If your router and devices support it, enable it. If not, use WPA2. Outdated security protocols, like Wired Equivalent Privacy (WEP), can be cracked very easily.
Turn off SSID broadcasting
By default, SSID broadcasting is turned on to help devices find and connect to your network. Turning it off won’t stop determined attackers using advanced software, but it’ll reduce your network’s visibility to opportunistic wardrivers.
Add a guest network with restrictions
If you often allow others to connect to your Wi-Fi, you might want to set up a secure guest network. This is especially important if you host an Airbnb or if your home doubles as a business.
A guest network is a separate Wi-Fi network that runs alongside your main one, designed specifically for visitors or untrusted devices. It allows people to use your internet connection without giving them access to your personal files, devices, or administrative settings.
This means your main network will be more isolated. With an extra layer of protection against malicious wardrivers, you’ll limit the potential damage they can cause.
Install a firewall and security software
Many routers come with basic firewall settings that help block unauthorized access attempts, but dedicated firewall software provides stronger, more customizable protection. Pairing a firewall with antivirus software further enhances your security.
Use multi-factor authentication for router access
Some modern routers support two-factor authentication (2FA). When 2FA is enabled, an attacker won’t be able to access the admin panel without having both your router’s admin password and a time-sensitive, single-use authentication code delivered via SMS, email, or an authenticator app.
FAQ: Common questions about wardriving
Is wardriving still a real threat today?
Yes, wardriving is still relevant today. There’s a chance that an attacker could discover the password of a particular Wi-Fi network just by driving through a neighborhood. This is in large part due to the prevalence of weak Wi-Fi passwords.
Can wardriving be detected or traced?
It’s very difficult to detect if the wardriver is only passively listening to broadcast signals. This is how Kismet, one of the most popular options when it comes to wardriving software, functions. A wardriver who’s actively scanning (e.g., by sending out probe requests) or attempting to connect to networks is much easier to trace, but even then, you’ll need to know what to look for.
How does wardriving affect home and business Wi-Fi?
When someone wardrives, they collect data about nearby Wi-Fi networks, including their security settings. If your Wi-Fi network is open or uses outdated security, this information can reveal that your network is vulnerable. Threat actors may use this intel to intercept your traffic or gain unauthorized access to your network or devices.
For home users, this may mean that the attacker steals your login credentials or credit card details. For businesses, this has resulted in devastating data breaches in the past.
Why do people wardrive?
People wardrive for many different reasons. Some wardrivers are hobbyists who just like to make maps. Other wardrivers may be researchers or ethical hackers out to identify vulnerabilities in an organization’s Wi-Fi.
That said, there’s no denying that a great many people wardrive in order to find security vulnerabilities that they can exploit for personal gain.
Is wardriving legal or illegal?
Wardriving is legal in most countries, since it generally involves only collecting data that’s being publicly broadcast by Wi-Fi access points. However, some countries have stricter laws. In those countries, wardriving may be illegal or fall into a legal grey area due to privacy reasons or because wardriving could be considered the prelude to a future crime.
Using data collected through wardriving to access a network without permission is illegal in almost all circumstances.
What should I do if I suspect wardriving?
If you’re worried about wardriving, there are a few things you can do to protect yourself. You can make sure its firmware is up to date, set strong Wi-Fi and router passwords, and install a firewall and/or antivirus on your devices. You can also check if you're using the highest security protocol for your Wi-Fi network, turn off Service Set Identifier (SSID) broadcasting, create a guest network, and enable two-factor authentication (2FA) on your router.
For maximum protection, I recommend installing a VPN on your router. Not every VPN can be installed directly on a router, but ExpressVPN offers routers that come with a VPN preloaded.
What’s the difference between wardriving and warwalking?
They’re basically the same thing. The only difference is whether the wardriver is moving around in a vehicle or on foot.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN



















Comments
Great articles, keep up the good work. TY lb
How do I access pluto tv and other free networks in the USA if I am in South Africa.